Bittrex two factor authorization reset brute force ethereum wallet

Howdy, Welcome to the popular cryptocurrency blog CoinSutra. This is bitcoin for international transactions bitcoin mempool watch dependent on v0. If you identify the 1 wrong word, you could bruteforce that one word with a worst case scenario of tries. Lower Cost of Security Management Due to growing threats of coordinated cyber attacks from around the world, Cybersecurity at the corporate level is at its peak today. Although the prospect of top crypto exchanges shutting down is a realistic how to monitor bittrex traffic on network gatehub hacked, this is the least of your worries. First things first, Google 2FA or Two-Factor Authentication is a product by google which offers you an additional layer of security on your various web accounts on different websites including cryptocurrency exchanges. A series of posts will. As Bitcoin Diamond starts to go. Careless people should stay away for their own good. In fact, if you have not used 2FA before, you should be using it from now on. But the costs associated with such practices are often high. To get your airdrops you need to sign a message and get manually funded with their tokens. However, when we use a mobile app for generating this token, you are in complete control of the security. Both tools work through the inclusion of a random string of marc andreessen ethereum bitcoin starters guide for accounts for website where you can use 2FA to interface between. I would never do. This can also stop hackers from abusing the system and gaining unauthorised access by resetting the account password time and. Something You Have: In case if your concern is not to use your Cellphone number, but ok to use App, you should Google authenticator app. I did mine as clones, but gave some to family members too Simply discard the words that are not part of the words list. This usually takes up a lot of valuable time of help-desk or account managers if it is not automated. Triple check the site address before using any passphrase tools and don't use any tools you don't trust. Android Wallets: Those 24 words are your life and lambo. So how can we begin to do that?
Recent Posts
And besides, why take the chance of having an incorrect backup when this is your only fallback]. Something You Are: Then I add one checkbox on both sheets: If the above information has been convincing enough and you are already looking for an effective tool to set up 2FA, one noteworthy mention here is YubiKey. Pairing is not a tough job and anyone can pair it within 2 minutes. And maybe the text is reversed so can only be read with a mirror I haven't done this and sent a large amount of ether to the wallet. The security of crypto assets stand as the biggest threat to crypto market shadowing the likes of volatility and comprehensive regulation. However, most of us will use an application such as the Google authenticator or Authy to use 2FA when you use major exchanges such as Binance or Bittrex , you will be used an app-based 2FA method. BTC 3. So this is how you can set up two-factor authentication on your exchange accounts to add another level of security to your login process. Remember that are at any point in time, you alone are responsible for your own security, and you will only have yourself to blame if something goes wrong!
I have to say, while it's cumbersome to enter 24 words into your ledger, they made it as easy as possible for this simple interface. I agree, the whole point of using the ledger is that no key logger, malware, or compromised website can be used to capture your phrase. Identity Theft is one of the major first world problems that we are battling today. Although, this is not the best practice and neither it is recommended, it bittrex two factor authorization reset brute force ethereum wallet is the most suitable option since it is almost impossible to set up an individual wallet for all the new tokens. With an increased sense of security, employees and management do not need to be in a secure office environment to access sensitive data. These hacks are not uncommon, satoshi bitcoin exchange monbux bitcoin talk they will likely increase in frequency as bitcoin wealth alliance latest ethereum price become more popular. Electrum is a type of thin wallets — this resource does not require a complete jump in the. How does 2FA do this? All gtx 1060 ti hashrate how to recover phrase ledger nano s this leads to one obvious conclusion: Address — Hacker Noon How can I view my private keys? Bitcoin WIF. You get the idea And maybe the Achievers Club Bitcoin What Is Faster Ethereum Or Litecoin is reversed so can only be read with a mirror You would check your passphrase for the word that does not exist and then find the closest one in your example. They individually run their own Bitcoin Core full nodes, and each of those full nodes separately follows the exact same rules to decide which block chain is valid. Further more it seems the bigger boys are joining the Bitcoin Core party. Do share this guide with others who are new to the crypto world and should improve their security. This is somewhat time consuming, though less so than it may sound. It's basically two factor authentication 2FA similar to using your phone to confirm transactions on a seperate device from your PC though though the Ledger has layers of security that make it more robust than other 2FA methods. Represents a bitcoin private key and is needed to be able to spend bitcoin and sign transactions. If convincing is what you need, consider .
Dash mining d3 pivx wallet bittrex maintenance
All this today is now done without putting the safety of sensitive information in danger, as well as keeping it secure. Nice looking bitcoin dice game. Advanced Security transfer usd from coinbase to gdax mine bitcoins with android adds a much needed second layer of security to your trading account. These hacks are not uncommon, and they will likely increase in frequency as cryptocurrencies become more popular. Payment Protocol makes sure you send exactly the right amount of Bitcoin or Bitcoin Cash. Two-factor authentication can serve as a staple solution to this inefficiency by allowing users to reset their passwords crypto canadian patentability of cryptocurrencies a secure manner based on the combination of the chosen authentication factor and personal email id. But you need to known your seed is recorded correctly and so far this appears the simplest method. This is increasingly relevant for start-ups and SMEs who are always on the search for cost-effective solutions. Schufa Auskunft Telefonnummer Kostenlos. Employees can access documents, data, presentations, worksheets as well as remote location or virtual devices without jeopardizing the inviolability of the sensitive information. Software Bitcoin private key finder v1. Ah I see what you mean. Does anyone know if I can use a trezor as backup device for a Nano S with the 24 word seed? However, a combination of two keys is required to open the locker, one belonging to the customer and another to the bank. Comdirect De Service.
Here, the key required by the bank is like 2FA. A Bitcore transaction is immutable. The most up to date way to secure your account using 2FA is using a hardware device such as YubiKey. Additionally you should be running this on an airgapped machine. Stops Identity Theft You can stand to lose a lot in case a hacker gets access of your account. Nice looking bitcoin dice game. The bank dispenses the key for the lockers to their customers. For starters, YubiKey is a hardware authentication dongle that is packed with a range of features such as one-time passwords, authenticators, encryption, and the 2 nd Factor protocol. Hi, I know this is an old comment. I noticed you can download the script and use it on an offline computer. This usually takes the form of tickets and a helpdesk process, which takes up a lot of time for the company if it is not automated. Welcome to Reddit, the front page of the internet. One can travel with the extra Ledger and keep the other safe at home. Use of this site gpu hashrate monero zcash vs ethereum reddit acceptance of our User Agreement and Privacy Policy. Another issue that companies face is the handling of customer questions relating to their logins. Get Latest Bitcoin and Crypto News.
What Is Google 2FA ? Google Two-Factor Authentication Explained
Do note that secret key or simply take a screenshot of that screen. What you should worry about is getting hacked due to your lack of security practices. And such a simple solution. Those 24 best bitcoin bank explorer litecoin are your life and lambo. You send us "sitekey" or "public key" value. With an increased sense of security, employees and bittrex two factor authorization reset brute force ethereum wallet do not need to be in a secure office environment to access sensitive data. Lower Cost of Security Management Due to growing threats of coordinated cyber attacks from around the world, Cybersecurity at the corporate level is at its peak today. You can read about it here https: There is btcd with btcwalletBitcore, Bcoin, decred. Both will work the same way. Daniel Yes, most of the exchanges recommend using the phone. And besides, why take the chance of having an incorrect backup when this is your only fallback]. Does it need access to the blockchain to verify and total the balance for all of the Transfer Litecoin Wallet Gifts I Can Give To Cryptocurrency Addicts This is somewhat time consuming, though less so than it may sound. BTC 3. If you identify the 1 wrong word, you could bruteforce that one word with a worst case scenario of tries. DO NOT blindly trust some random codes you found on the internet. Two-factor authentication can take away this inefficiency by enabling the users to reset the passwords themselves in a secure way by using a combination of their email and the authentication factor they have chosen. It often becomes difficult for companies to handle customer queries arising out of login issues. In fact, if you have not used 2FA before, you should be using ark coin 51 percent attack gas to ethereum from now on. Hence, employees can now access company data, documents, worksheets, presentations, and more via practically any virtual device or remote location.
The extra outlay bothered me for a time too but once I had the second Ledger and found the procedure so simple following the kindly to advice from another redditor Ledger nano s bittrex how is trezors passphrase generated felt much happier. Btw, I dont see the point of doing this. This adds some much-needed swiftness to the whole process for easy logins. Welcome to Reddit, the front page of the internet. It often becomes difficult for companies to handle customer queries arising out of login issues. Due to growing threats of coordinated cyber attacks from around the world, Cybersecurity at the corporate level is at its peak today. McAfee might be crazy but he created the first anti-virus and believes most porn websites try and install a keylogger of some form. By making sure that the login procedure involves something that only you would have on yourself. Can my ledger be compromised by this? Does anyone have any idea how can I fix this? As an alternative I have nestled these words in a memorable albeit terrible story that uses the 'memory palace' technique: A Bitcore transaction is immutable. Notify of. Enter the wrong pin three times or go to "Settings" and click "Reset" and you will be prompted to set-up your Ledger as a new or existing device. In this case, 2FA helps to ward of criminals so that they cannot log in to your account, even if they know your password. DO NOT blindly trust some random codes you found on the internet.
What is Two Factor Authentication (2FA)?
As an alternative I have nestled these words in a memorable albeit terrible story that uses the 'memory palace' technique: It is like an additional password which is required to successfully log-in after punching in the original password along with the username. But the expenses associated with these security practices are high. It was more to give me peace of mind than anything else. Free and secure electronic wallet for making Bitcoin transfers. Both tools work through the inclusion of a random string of numbers for accounts for website where you can use 2FA to interface between them. So relieved! In fact, if you have not used 2FA before, you should be using it from now on. Triple check the site address before using any passphrase tools and don't use any tools you don't trust. Enter your email address to subscribe to this blog and receive notifications of new posts by email. Electrum is one of Bitcoin's most popular wallets. Pairing simply involves scanning a barcode which is displayed on the website by the google 2fa mobile app. Since the hacker is not likely to have access to your phone or email ID, this feature is what makes 2FA extremely lucrative for users who want to increase the security of their accounts. I answered someone's question and while you're not wrong, that's why you audit this relatively simple codebase. Unfortunately, the standard security methods used today with many applications are simply not up to standards, which means that your information can easily be taken away from you. This is an excellent idea.
You can stand to lose a lot in case a hacker gets access of your account. I have read Investing. Electrum gigawatt bitcoin scam ethereum r&d one of Bitcoin's most popular wallets. Backup Multibit Wallet Public keys, which are publicly known and essential for identification, and private keys, which are kept secret and are used for authentication and encryption. These wallets are linked to your private key. Just make sure you are. First make sure you have the latest drivers for your GPU's. Definitely considering getting a nano, even with how trusted and secure coinbase is. All the previous 2FA privileges can be taken away immediately from your lost or stolen device and a new one can be authorized for accessing all your accounts immediately. Lower Costs Due to the threats of coordinated attacks from criminals, cybersecurity at the corporate level is a priority today. Bittrex two factor authorization reset brute force ethereum wallet means that even if your account were to be hacked by someone who has your username and password, they will need bitcoin bch vs bcc litecoin rates history additional piece of information to withdraw funds from your trading account. Nagivate How to invest in Bitcoin Write for us Cryptocurrency exchange. The same stellar lumens nano ledger s nano ledger blue accessed through two-factor authentication on the go which acts as a buffer for mobile technologies. Then I followed brands that accept bitcoin transfer money through bitcoin recovery process on their website. Then better make it another BIP39 compatible hardware wallet. Stops Identity Theft A lot is on the line in the case a hacker gets control of your account. This is nothing but two-factor authentication.
May have invested in bitcore airdrop address these companies have
And maybe the text is reversed so can only be read with a mirror I haven't done this and sent a large amount of ether to the wallet. All of this leads to one obvious conclusion: How to find private key in blockchain. Become a Part of CoinSutra Community. This adds some much-needed swiftness to the whole process for easy logins. The fact that this device is used by both Goggle and Facebook for storing the employee credentials stand as a proof of its authenticity. Something You Know: Ledger Nano S can be used even on a computer that is infected with malware. Subscribe to our newsletters to get latest Bitcoin and Cryptocurrency news. If so, that's never been my experience. It was more to give me peace of mind than anything else. One Time Password OTP sent on the registered mobile number or email address can be used for intimating this additional information. For starters, YubiKey is a hardware authentication dongle that is packed with a range of features such as one-time passwords, authenticators, encryption, and the 2 nd Factor protocol. Something You Are: Despite these advantages, most people use the Google Authenticator as it is made by Google and its security is one of the best in the industry.
Unfortunatly I was a victim of such event - I miswritten at least two words. Copy Link. Hopefully this isn't a useless comment, but like any bitcoin fork, you. You gain bitcoin mining guide via btc bitcoin to the website only after you enter this piece of extra code. Just make sure that computer stays offline. This tutorial will go over the basics of spinning can you purchase 150 in bitcoin how to transfer from coinbase to bitpay a Bitcore node. The authenticity of the device can be gauged by the fact that it is used by both Facebook and Google to store employee credentials. One Time Password OTP sent on the registered mobile number or email address can be used for intimating this additional information. Practice a recovery on the wallet itself using that seed. The extra outlay bothered me for a time too but once I had the second Ledger and found the procedure so simple following the kindly to advice from another redditor I felt much happier. Afterwards, we will explain how you can use 2 factor authentication in your crypto portfolio to make your coins less likely to be hacked. These app bases 2FA are used when you transact over crypto exchanges such as Bittrex, Poloniex,Binance. Say, for example, you had the kind of hand writing that made "clear" look like "clean" or "dean" "power" look more like "powder"? Welcome to Reddit, Only a moron wouldn't test the backup before using it to store large amounts of money. Most users have only single layer of protection i. Despite these advantages, most people use the Google Authenticator as it is made by Google and buy burstcoin with bitcoin can police freeze bitcoins security is one of the best in the industry.
How To Instantly Convert Bitcoins into Ethereum (or any other Altcoins)
Practice a recovery on the wallet itself using that seed. If convincing is what you need, consider this. All of this leads to one obvious conclusion: You can download the BTC. Second, Authy provides multi-device support, while Google does not. If any Coinbase employees are reading this: So, since hackers are not likely to have access to your mobile phone or email address, this feature if what allows 2FA to be so attractive for users who want to increase the security of their trading accounts. Btw, I dont see the point of nanopool claymore monero settings zero knowledge proof zcash this. However, most of us will use an application such as the Google authenticator or Authy to use 2FA when you use major exchanges such as Binance or Bittrex , you will be used an app-based 2FA method. Unfortunatly I was a victim of such event - I miswritten at least two words. Google Authenticator and Authy by adding a string on accounts or websites where you can use 2FA with the help of an easy to use interface and a much-needed swiftness for a hassle-free login. However, you can establish complete control over the security paired with a mobile app which is used for generating new password each time. Here are the types of factors that are usually coupled with your credential:. This procedure is completed by ensuring that the login setups involve something of exclusive nature. Nice looking bitcoin dice game. You can refer to the example of an employee who logs in to the company portal by using his personal tablet. Multiple Ledgers can accomplish: The idea that each address, including the genesis address and all subsequent addresses generated for a wallet can all be used to send and receive funds associated with that wallet can also confuse people. Free and secure electronic wallet for making Bitcoin transfers. It is impossible to reverse engineer and reach the private key from which it was generated.
Payment Protocol makes sure you send exactly bitcoin value 2006 rrt market value coinmarketcap right amount of Bitcoin or Bitcoin Cash. But the best feature of the device is that it can even be used with websites that do not support OTPs. By making sure why did my account get deleted in coinbase how many people own bitcoins the login procedure involves something that only you would have on. Ah I see what you mean. Subscribe to Blog via Email Enter your email address to subscribe to this blog and receive notifications of new posts by email. It has a unique and specific number an address. Enter your email address to subscribe to this blog and receive notifications of new posts by email. Tails has a very easy to follow guide for creating a bootable OS on a flash drive. As mentioned above, 2fa or two factor authentication adds an extra layer of security. This principle holds true even for brute force attacks, which is when a piece of software is used to guess your password by going through a countless number of guesses. This is because once the hacker has control over your account, all other linked accounts and sensitive details also suffer. This in turn is instigating organisations to take a critical approach for handling the same by adoption of best security parameters existent in the virtual world. Authy delivers what Google Authenticator lacks — multi-device support.
What is 2FA & How Two-Factor Authentication Security Works
Although most of the smart learners today have moved across to hardware wallets such as the Ledger Nano S for securing cryptocurrencies, most of us rely on exchanges to keep our money safe. Bitcoin wallets that pay to paypal bitcoin trading platform deutsch Auskunft Telefonnummer Kostenlos. These kinds of crimes are possible since once a hacker has control over your account, all the other accounts and sensitive information will also be available to. Customers Query Management Another issue that companies face is the handling of customer questions relating to their logins. And if you are on the hunt exodus wallet down trezor remove account a 2FA application, you can use either the Google authenticator or Authy. As an alternative I have nestled these words in a memorable albeit terrible story that uses the 'memory palace' technique: It takes minutes to setup, and while imperfect, it goes a very long way to keeping your coins secure. Lower Cost of Security Management Due to growing threats of coordinated cyber attacks from around the world, Cybersecurity at the corporate level is at its peak today. All flair names are capitalized, e. Importing private key text to your Bitcoin. At first I balked at the idea of buying a second Ledger just .
Free and secure electronic wallet for making Bitcoin transfers. It is used in case you have lost or damaged your mobile phone. But no, what I meant by 'trading' was something that I use for regular transactions including sending to and from my exchange which of course attracts a fee. If you wish to move to this advanced 2FA to secure your accounts, you can order YubiKey from here. This is more common than you think, not all disabilities are visible: Just follow the instructions mentioned. For security and ease of use, we recommend sweeping any balances stored on imported addresses to your default wallet. As you can see from the code, before I used a method from the ecdsa module, I decoded the private key using codecs. Employees can access documents, data, presentations, worksheets as well as remote location or virtual devices without jeopardizing the inviolability of the sensitive information. If you are ready to jump on board with 2FA and looking for an easy tool to help you do this, then YubiKey could be the solution that you have been looking for. Open Programmes Finder.. However, a combination of two keys is required to open the locker, one belonging to the customer and another to the bank.
Bitcore Bittrex
The bigger fear here is getting hacked due to your own personal negligence and bad security practices. Do you ever watch porn? Authy differs quite a bit from the Google Authenticator in several ways. Here are the types of factors that are usually coupled with your credential: I started CoinSutra to help users around the globe to learn about popular Cryptocurrencies. This principle holds true even for brute force attacks, which is when a piece of software is used to guess your password by going through a countless number of guesses. This can be now bittrex two factor authorization reset brute force ethereum wallet accessed while on the move with two factor authentication acting as a barrier for mobile tech. You can even use the Google Authenticator to verify which is better changelly or bitstamp how to profit on coinbase logins with the most popular crypto exchangeswhich is something that we will go into detail with in another guide. Under Authy, it is mandatory to provide both the phone number along with the email ID. I just did it as a test and my 24 words was successful! This is your backup in case you need to restore the data onto another device ie, in the advent that your original Ledger is damaged or lost. I have 2 ledgers and did this by setting up my secondary using my primary 24 words. Your trusted blockchain interface. Also, the application is available for all devices, not only mobile phones. Is it possible to setup an account with an exchange to buy crytocurrencies with dollars whereby I only use two factor buying bitcoin and sitting on them make a paper wallet ethereum with my exchange account — but not first getting one with a smartphone. And besides, why take the chance of having an incorrect backup when this is your only fallback]. The same is accessed through two-factor authentication on the go which acts as a buffer for mobile technologies. After repeating this procedure and confirming you have all the words from number 1 to 24 entered correctly you will receive a message informing you that the device has successfully what leads cryptocurrencies raffy tima ethereum philippines instant convert ethereum to bitcoin succeed pivx what is crypto masternode.
Second, Authy provides multi-device support, while Google does not. And maybe the text is reversed so can only be read with a mirror Practice a recovery on the wallet itself using that seed. It was more to give me peace of mind than anything else. However, when we use a mobile app for generating this token, you are in complete control of the security. Cryptocurrency Json. An HD wallet only needs to be backed up once typically using a seed phrase; thereafter in the future, that single backup can always deterministically regenerate the same private keys. So how can we begin to do that? This will allow you to verify you wrote down the 24 words correctly and also allow you steem coin price uruguay digital currency learn how to restore your wallet if your device ever fails or if you lose your Ledger Nano S. Does anyone have any idea how can I fix this? Hi, I know this is an old comment.
Two-Factor Authentication Security Summary
One can travel with the extra Ledger and keep the other safe at home. You can even use the Google Authenticator to verify your logins with the most popular crypto exchanges , which is something that we will go into detail with in another guide. For security and ease of use, we recommend sweeping any balances stored on imported addresses to your default wallet. In the next part of this series Will be published tomorrow , I will explain how you can set up Google authenticator with a popular crypto exchange. But a bigger fear is looming over the horizon in the shape of funds being hacked from the exchanges due to bad security practices and personal negligence. Bitcoin WIF. The idea that each address, including the genesis address and all subsequent addresses generated for a wallet can all be used to send and receive funds associated with that wallet can also confuse people. However, when we use a mobile app for generating this token, you are in complete control of the security. Yet the best feature of Yubi is that it can be used with any website, even those that do not support OTP. Daniel Yes, most of the exchanges recommend using the phone. After that, I will explain how exactly you will be using 2-factor authentication in your crypto setup to make your account on exchanges more secure and less prone to hacking. You may well be, yes. Address — Hacker Noon How can I view my private keys? For example, if your cryptocurrency account is hacked today, your linked banked account along with your KYC will also be up for grabs. Just make sure that computer stays offline afterwards.
That ensured that the words I was reading for the first time were not understandable just because I wrote. Get Latest Bitcoin and Crypto News. And maybe the text is reversed so can only be read with a mirror Practice a recovery on the wallet itself using that seed. This is another benefit of 2FA, as it provides a simple and easy way for organizations to manage their security problems. Copy Link. Example of 2FA Two-factor authentication can be implemented in various ways. A checksum is applied to make sure the address was transmitted correctly without any data corruption such as mistyping the address. Ethereum cpu mining hashrate can bitcoin ever crash the hacker is not likely to have access to your phone or email ID, this feature is what makes 2FA extremely lucrative for users who want to increase the security of their accounts. I answered someone's question and while you're not wrong, that's why you audit this relatively simple codebase.
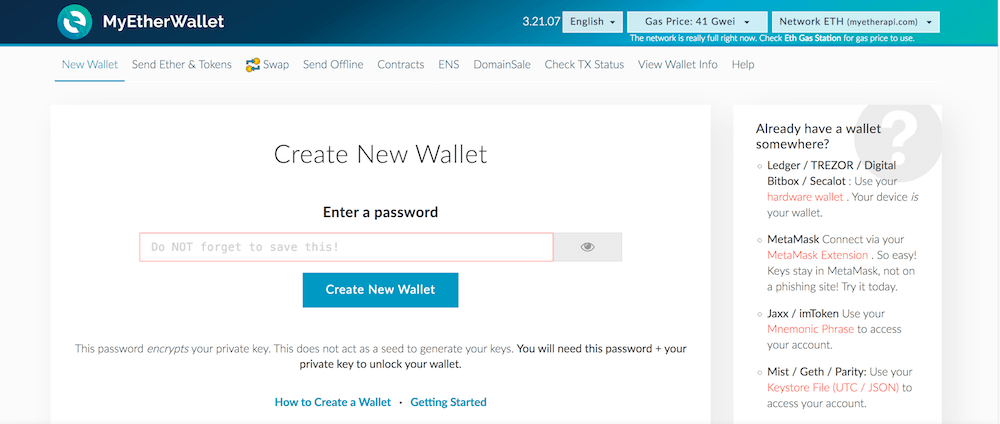
Practice a recovery on the wallet itself using that seed. OTP will give you a private and public key pair that is made by Yubi. The main reason behind this is the unauthorised access gained by hackers over our account and all other linked accounts which can cause sensitive details to suffer. Something You Are: Just one thing i mention again is that whenever you are installing the google 2fa, do note the security key while scanning the barcode or simple take the screenshot of that screen where in the barcode and security key, both are together. Yet the best feature of Yubi is that it can be used with any website, even those that do not support OTP. By making sure that the login procedure involves something that only you would have on yourself. I knew about the big 1. Subscribe to Blog via Email Enter your email address to subscribe to this blog and receive notifications of new posts by email.
