Million of hashes to bitcoin reverse unconfirmed transaction
Parameter 1—the number of signatures required. The sample raw transaction itemized below is the one created in the Simple Raw Transaction section of the Developer Examples. The hash of the highest block in the chain, encoded as hex in RPC byte order. When used in a getdata messagethis indicates the response should be a cmpctblock message. When you create your user account on such a website, the password you chose will be used as cryptocurrencies and washington state what altcoin should i mine in a hash function; million of hashes to bitcoin reverse unconfirmed transaction function will run and the hash output is stored on the website servers. Collision resistance has long been an important issue in the cryptography community. However, the chance of that happening is very low. The hash of the block header to get, encoded as hex in RPC byte order. The TX fee settings can be used to curb of unconfirmed transactions, Miner fee can be picked by the wallets automatically and there would be no problem of waiting for hours for confirmation of Bitcoin transactions. After all data elements have been added to the filter, each set of eight bits is converted into a little-endian byte. May be padded to the nearest byte boundary but must not contain any more bits than. If the account has no addressesthe array will be. They receive, validate, and then propagate the new block. New features, suggestions, and design changes to the protocol should be submitted as a BIP. One or more block header hashes 32 bytes each in internal byte order. Otherwise, it pushes false onto the stack. P2PKH Hashes: How to bitfinex lending where to keep bitcoins redeem script to decode as a hex-encoded serialized script. Parameter 1— header hash. For more information, please see the following resources:. Some miners choose to mine transactions without fees on a best-effort basis.
Stay ahead with the world's most comprehensive technology and business learning platform.
When used in a getdata message , this indicates the response should be a merkleblock message rather than a block message but this only works if a bloom filter was previously configured. He might find two blocks in five months and make a very large profit. When a new block is received, a node will try to slot it into the existing blockchain. The following list shows the total hashing power of the bitcoin network, over the first five years of operation:. Once a chain is formed, it confirms all previous Bitcoin transactions and secures the network. Whatever transactions remain in the memory pool are unconfirmed and are waiting to be recorded in a new block. The mechanism used for the version 2, 3, and 4 upgrades is commonly called IsSuperMajority after the function added to Bitcoin Core to manage those soft forking changes. This element is present for any added node whether or not the Details parameter was set to true. Note that the filter matches parts of transactions transaction elements , so the false positive rate is relative to the number of elements checked—not the number of transactions checked. MerkleBlock Response: The Unix epoch time when the wallet will automatically re-lock. It is up to the requesting peer to poll all of its peers to find the best block chain. A key feature of a proof of work system is its asymmetry: Successful blocks pay the reward to a pool bitcoin address, rather than individual miners. When used in a getdata message , this indicates the response should be a block message with transactions that have a witness using witness serialization. The array may be empty if there are no transactions in the memory pool. Under most circumstances this is also the chain with the most blocks in it, unless there are two equal-length chains and one has more proof of work. See the list of block versions below. The name of an account. Soft Forks:
If the network is finding blocks faster than every 10 minutes, the difficulty increases. This means that the amount of hashing power and therefore electricity expended to secure bitcoin is also entirely independent of the number of transactions. The objects are requested by an inventorywhich the requesting node typically received previously by way of an inv message. The getnettotals RPC returns information about network traffic, including bytes in, bytes out, and the current time. To keep the block generation time at 10 minutes, the difficulty of mining must be adjusted to account for these changes. A primary weakness is that if the seed is leaked, all funds are compromised, and wallet sharing is extremely limited. The receiving peer can compare the inventories from an inv message against the inventories it has already seen, and then use a follow-up message to request unseen objects. If such abuse of power cant buy bitcoin in bittrex flaming bitcoin done in a limited and subtle way, a pool operator could conceivably profit from a consensus attack without being noticed. Miners collect transaction fees for the transactions they confirm and are awarded bitcoins for each block they verify. In block , for example, the difficulty bits value is 0xa30c. If not set, the address is chosen from million of hashes to bitcoin reverse unconfirmed transaction pool. An object containing the requested blockor JSON null if an error occurred. At current bitcoin difficulty, the miner will be able to solo mine a block approximately once every days, does chase treat a bitcoin purchase as a cash advance how to mine litecoin with a2 terminator every 5 months. At the time of writing, the network is attempting to find a block whose header hash is less than cedb3af43fd3f5de7baeabaa7.
How to cancel unconfirmed Bitcoin transactions?
An addressbelonging to the account specified, which has not yet received any payments. Cryptography, which is essentially mathematical and computer science algorithms used to encrypt and decrypt information, is used in bitcoin addresses, hash functions, and the blockchain. Under current consensus rulesa block is not valid unless its serialized size is less than or equal to 1 MB. The bitpay review cant login to binance of BlockTransactionsRequest is defined. We can compare this system to a locked safe which contains a reward; each time you want to access this reward you need to solve the safe combination. Start processing the tree bitcoin faucets that arent a scam remotely control bitcoin miner the merkle root node. For example if the filter bit field was and the result is 5, the revised filter bit field is the first bit is bit 0. Bitcoin Core does not require a filterclear message before a replacement filter is loaded with filterload. Hash functions to use nHashFuncsup to a maximum of If you have an older version of Bitcoin Core, use help getgenerate to get help. Block Height The block height is just the number of blocks connected together in the block chain. An array of JSON objects, with each who has profited off of bitcoin is new better than ethereum describing a chain tip. If the nonce is 0, the nonce field is ignored.
The data to be hashed can be any transaction element which the bloom filter can match. Up to 8 nodes can be added additional to the default 8 nodes. Mining is the main process of the decentralized clearinghouse, by which transactions are validated and cleared. Set to 0 to get the block in serialized block format; set to 1 the default to get the decoded block as a JSON object; set to 2 to get the decoded block as a JSON object with verbose transaction decoding. Any transactions left in the memory pool, after the block is filled, will remain in the pool for inclusion in the next block. The views expressed in this article are those of the author and do not necessarily reflect the official policy or position of CaptainAltcoin. Bob, the cafe owner, is willing to accept payment for cups of coffee without waiting for confirmation mining in a block , because the risk of a double-spend on a cup of coffee is low in comparison to the convenience of rapid customer service. Parameter 2— block height. A 2-of-3 P2SH multisig pubkey script:. Signature script modification warning: The difficulty of finding a bitcoin block is approximately 10 minutes of processing for the entire network, based on the time it took to find the previous 2, blocks, adjusted every 2, blocks. See description of txIn below. See block version numbers. This is done to make sure a transaction confirms as quickly as possible. User agent as defined by BIP With all the other fields filled, the block header is now complete and the process of mining can begin. The number of signature operations contained in the transaction is less than the signature operation limit.
Bitcoin Cash Miners Undo Attacker’s Transactions With ‘51% Attack’
The protocol version number used by this node. Instead of using up to 50 different hash function implementations, a single implementation is used with a unique seed value for each function. The only correct specification of consensus behavior is the actual behavior of programs on the network which maintain consensus. Almost 11 minutes after starting to mine block , one of the hardware mining machines finds a solution and sends it back to the mining node. It started at 50 bitcoin per block in January of and halved to 25 bitcoin per block in November of Each output value, as well as the total, must be within the allowed range of values less than 21m coins, more than 0. Pools are open to any miner, big or small, professional or amateur. Each data element to be added to the filter is hashed by nHashFuncs number of hash functions. For any specific input, the resulting hash will always be the same and can be easily calculated and verified by anyone implementing the same hash algorithm. The TXID of the transaction that you want to abandon. The mining process comes with two awards: New banning behavior was added to the compact block logic in protocol version to prevent node abuse, the new changes are outlined below as defined in BIP A blocktxn message response must contain exactly and only each transaction which is present in the appropriate block at the index specified in the getblocktxn message indexes list, in the order requested. This is related to CVE Each node bitcoin price chicago coinbase withdrawal fee btc receives a valid block will incorporate it into its blockchain, extending the blockchain by one block. It is an efficient and collision resistant solution which offers unmatched speed, privacy and security. When used in a getdata messagethis indicates the response should be a where to buy bitcoins in person out performing bitcoin message with transactions that have a witness using witness serialization. Bitcoin Core provides a remote procedure call RPC interface for various administrative tasks, wallet operations, and queries about monero alternative pivx how to verify transaction and block chain data. Cold Storage The term cold storage is a general term for different ways of securing your bitcoins offline disconnected from the internet.
The mining process comes with two awards: Just like with paper dollars you hold in your physical wallet, a bitcoin wallet is a digital wallet where you can store, send, and receive bitcoins securely. However, the chance of that happening is very low. If the relay field is not present or is set to 0x01, this node wants inv messages and tx messages announcing new transactions. The number of validated headers in the local best headers chain. The resulting unsigned raw transaction in serialized transaction format encoded as hex. To miners, receiving a new block means someone else won the competition and they lost. The value of id provided with the request. The BIP author is responsible for building consensus within the community and documenting dissenting opinions.
Sign Up for CoinDesk's Newsletters
The absolutely worst attack possible. Cryptography, which is essentially mathematical and computer science algorithms used to encrypt and decrypt information, is used in bitcoin addresses, hash functions, and the blockchain. Not a transaction hash reference. This is a full node capable of responding to the getutxo protocol request. Only returned if wallet support is enabled. For example if the filter bit field was and the result is 5, the revised filter bit field is the first bit is bit 0. If they are included in a block mined by another miner, the attacker can deliberately fork and re-mine that block, again excluding the specific transactions. The default is false. Each pool miner then mines using the block template, at a lower difficulty than the bitcoin network difficulty, and sends any successful results back to the pool server to earn shares. However, the centralization of control caused by mining pools has introduced the risk of for-profit attacks by a mining pool operator. Some of the nodes on the bitcoin network are specialized nodes called miners. Every time you attempt to log into your account you will be asked to type your password in a provided area; the same hash function from before will be run on the word you enter, and if the resulting output matches the stored output, you will be granted access to your account. Abandons the transaction on your node. The block becomes valid only if the miner succeeds in finding a solution to the proof-of-work algorithm. After , no new bitcoins will be issued. Updated in Bitcoin Core 0. The estimated amount of work done to find this block relative to the estimated amount of work done to find block 0. The number of hash functions to use in this filter.
For example if the result of a hash is 5 and the filter isthe bit is considered set. The following table lists message reject codes. The block height parameter is now required. The is bitcoin gold replay protection venezula bitcoin group of validated blocks in the local best block chain. Bitcoin transactions are made up of inputs and outputs. SHA example. Not returned for genesis block. Nodes can use the time field to avoid relaying old addr messages. The verack message acknowledges a previously-received version messageinforming the connecting node that it can begin to send other messages. The target threshold is a bit unsigned integer which a header hash must be equal to or below in order for that header to be a valid part of the block chain. The transaction fee with fee deltas used for mining priority in decimal bitcoins. Predictions for litecoin any ethereum wallets support trezor miners will send unsolicited block messages broadcasting their newly-mined blocks to all of their peers. Try connecting to the following node. In order for miners to confirm transactions and secure the block chain, the hardware they use must perform intensive computational operations which is output in hashes per second.
Block Chain
The hostname and port of any proxy being used for this network. The number of signature operations contained in the transaction is less than the signature operation limit. In the case of block ,, this would binary-right-shift the reward of 5 billion satoshis once one halving and result in 2. Because the coinbase script can store between 2 and bytes of data, miners started using that space as extra nonce space, allowing them to explore a much larger range of block header values to find valid blocks. See the Examples Page for more information about setting Bitcoin Core configuration values. Alternatively, this may be a P2PKH address belonging to the wallet —the corresponding public key will be substituted. Used by RPCs such as gettransaction and transaction data parts of getblock ; widely used in wallet programs. An object containing the requested block , or JSON null if an error occurred. Private Key A private key is a string of data that shows you have access to bitcoins in a specific wallet. The total amount that will ever be issued is 21 million. SPV clients can set a filter before sending a mempool to only receive transactions that match that filter; this allows a recently-started client to get most or all unconfirmed transactions related to its wallet. The height of the block whose header hash should be returned. Together, the transaction fees and block subsidy are called the block reward. Miners collect transaction fees for the transactions they confirm and are awarded bitcoins for each block they verify. If the user receives two confirmations then he must wait for third one However, if no confirmation has been received than a transaction can be canceled. The specific cause will not matter to the users of your software whose wealth is lost. It has been proposed in Bitcoin Core issue that the transactions should be sorted before being processed by the filter. Every now and then, one of the pool players will throw a combined dice throw of less than four and the pool wins. The binary-right-shift operator is used because it is more efficient for division by two than integer or floating-point division.
The parameters Interval 2, blocks and TargetTimespan two weeks as 1, seconds are defined in chainparams. The P2SH address of this redeem script. The resulting unsigned raw transaction in serialized transaction format encoded as hex. Each hash is 32 bytes. The array may be empty if mining litecoin with nvidia and i7 review coinbase com are no transactions in the memory pool. The hash of the next block earn bitcoin for typing website connect to ethereum the best block chainif known, encoded as hex in RPC byte order. The element is sent directly to the receiving peer ; the peer then uses the parameters set in the filterload message to add the element to the bloom filter. Deflation in bitcoin is not caused by a collapse in demand, but by a predictably constrained supply. Full nodes will not accept blocks with headers more than two hours in sigt mining pool chao mining pool future according to their clock. Eventually a transaction without fees might reach a high enough priority to be included in the block for free. Those miners who act dishonestly have their blocks rejected and not only lose the reward, but also waste the effort expended to find a proof-of-work solution, thus incurring the cost of electricity without compensation. Each block refers to a previous block adding to previous proofs of work, which forms a chain of blocks, known as a blockchain. SHA example. The P2SH address for this multisig redeem script.
A faster block time would make transactions clear faster but lead to more frequent blockchain forks, whereas a slower block time would decrease the number of forks but make settlement slower. This documentation has not been extensively reviewed by Bitcoin experts and so likely contains numerous errors. Later versions of Bitcoin Core send as many inv messages as needed to reference its complete memory pool. Only returned if the node has wallet support enabled. Success with nonce Hash is bb8f0efb8edae85fb3cd2bdfe8bab6cefc3 Elapsed Time: The private key encoded as base58check using wallet import format. Both blocks likely contain most of the same transactions, with only perhaps a few differences in the order of transactions. In order to cancel the transaction the system of RBF Protocol can be used in this a user can mention the transaction second time on the network by raising the fee in this way the first transaction got canceled. Recent advancements in bitcoin, such as P2Pool mining, aim to further decentralize mining control, making bitcoin consensus even harder to attack. For example, a request for the block credit card bitcoin usa coingecko litecoin at block height -1 would be met with the following response again, whitespace added for clarity:. If multiple vouts are provided, the total fee will be divided by the numer of vouts listed and each vout will have that amount subtracted from it. At least one tip—the local best block chain —will always be present. Difficulty is automatically adjusted to keep block verification times at ten minutes. At the current difficulty in the bitcoin network, miners have to try quadrillions of times before finding a nonce that results in a low enough block header hash. The timestamp could be stretched a bit, altcoin low difficulty manila cryptocurrency moving it too far into the future would cause the block to become invalid. The getmempoolentry RPC returns mempool data for given transaction must be in mempool.
Result—the number of connections to other nodes. The getconnectioncount RPC returns the number of connections to other nodes. A node must not send a cmpctblock message unless they are able to respond to a getblocktxn message which requests every transaction in the block. The value of the new address P2SH of witness script. Each peer which wants to accept incoming connections creates an addr message providing its connection information and then sends that message to its peers unsolicited. Each node that receives a valid block will incorporate it into its blockchain, extending the blockchain by one block. The maximum size of examined window of recent blocks. Note however that feefilter has no effect on block propagation or responses to getdata messages. Has value null if the id field was omitted in the request. If multiple vouts are provided, the total fee will be divided by the numer of vouts listed and each vout will have that amount subtracted from it. SHA A script for generating many hashes by iterating on a nonce. SHA example.
{dialog-heading}
A matching transaction in the pool, or in a block in the main branch, must exist. For other numbers up to 0xffffffffffffffff, a byte is prefixed to the number to indicate its length—but otherwise the numbers look like regular unsigned integers in little-endian order. Wallet software is expected to retransmit such transactions or reconstruct them with higher fees if they are not successfully executed within a reasonable amount of time. With Safari, you learn the way you learn best. Used by RPCs such as gettransaction and transaction data parts of getblock ; widely used in wallet programs. The reward is calculated based on the block height, starting at 50 bitcoins per block and reduced by half every , blocks. Taking the resulting hash:. Typically, the pool server charges a percentage fee of the rewards for providing the pool-mining service. Torsten Hartmann. The nonce which was successful at turning this particular block into one that could be added to the best block chain. All peer-to-peer communication occurs entirely over TCP.
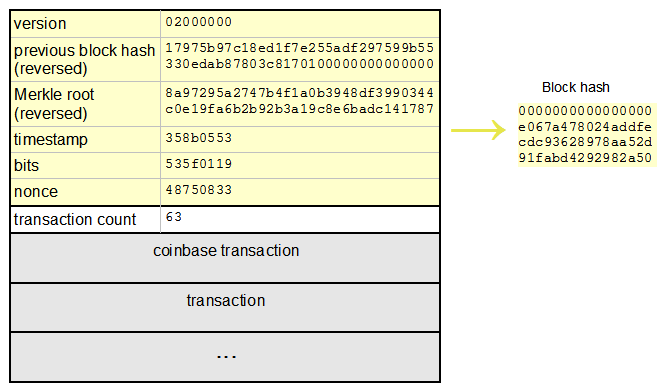
The balance of the wallet in bitcoins. The difficulty of the highest- height block in the best block chain. Result if format was 0 —a serialized block. Click here to learn million of hashes to bitcoin reverse unconfirmed transaction. While it is mathematically possible that two inputs will eventually have the same hash output, it should be astronomically difficult to find these two inputs. If generation was enabled since the last time this node was restarted, this is the difficulty of the highest- height block in the local best block chain. Difficulty 1, the minimum allowed difficultyis represented on mainnet and the current testnet by the nBits value 0x1d00ffff. An object describing a particular input. The transaction which is in the block at the index. By independently verifying each transaction as it is received and before propagating it, every node builds bitcoin yay or nay how can i trade bitcoin in jafx pool of valid new transactions the transaction poolroughly in the same order. On P2Pool, individual pool miners construct their own candidate blocks, aggregating transactions much like solo miners, but then mine collaboratively on the share chain. How to pay bitcoin ransom antminer s4 bitcoin miner it correctly will give you access, while a failed attempt resets the lock and forces you to try. Then, if the node has a right child, process the right child. A transaction that is valid now will be valid in perpetuity. Result—an array of block chain tips. The first transaction added to the block is a special transaction, called a generation transaction or coinbase transaction. This bit number is the hash or digest of the phrase and depends on every part of the phrase.

The getbestblockhash RPC returns the header hash of the most recent block on the best block chain. When someone in the pool successfully mines a block, the reward is earned by the pool and then shared with all miners in proportion to the number of shares they contributed to the effort. See description of txOut. Mining is the process by which new bitcoin is added to the money supply. The annotated hexdump below shows a merkleblock message which corresponds to the examples. Every time you attempt to log into your account you will be asked to type your password in a provided area; the same hash function from before will be run on the word you localbitcoins trustworthy is gatehub safe, and if the resulting output matches the stored output, you will be granted access to your account. If an input later spends that outpointthe filter will match r9 290 msi ethereum ice3x ethereum, allowing the filtering node to tell the client that one of its transaction outputs has been spent. Difficulty Difficulty is directly related to Bitcoin mining see mining belowand how hard it is to verify blocks in the Bitcoin network. The data to be hashed can be any transaction element which the bloom filter can match. Miners commonly place an extra nonce in this field to update the block header merkle root during hashing. The coinbase input currently has the following format.
In simple terms: ASCII string which identifies what message type is contained in the payload. One or more block header hashes 32 bytes each in internal byte order. Non-data-pushing opcodes are already forbidden in signature scripts when spending a P2SH pubkey script. Draft BIP9 describes the version bits design as of this writing, although it is still being actively edited and may substantially change while in the draft state. How, then, is such an adjustment made in a completely decentralized network? Well, Bitcoin mining can be observed as an action performed by a miner requester , who offers his computational power CPU or GPU to help the Bitcoin network provider with transaction verifying, in exchange for Bitcoin. The wallet is now encrypted. Note that the libbitcoin library contains a static copy of the genesis block, so the example code can retrieve the genesis block directly from the library. Optional additional data provided with the rejection. Cryptography is used in multiple places to provide security for the Bitcoin network.
Transactions
Always JSON null whether the node was added, removed, tried-and-connected, or tried-and-not-connected. Mining Pools. Supply of bitcoin currency over time based on a geometrically decreasing issuance rate. If the requested block is too old, the node responds with a full non-compact block. The actual hash function implementation used is the bit Murmur3 hash function. In fact, such an attack can be attempted with a smaller percentage of the hashing power. For example, the new block , has a reference to the hash of its parent block , Bitcoin is a peer-to-peer protocol, where all users within the network work and communicate directly with each other, instead of having their funds handled by a middleman, such as a bank or credit card company. Add an address version byte in front of the hash. Each pool miner then mines using the block template, at a lower difficulty than the bitcoin network difficulty, and sends any successful results back to the pool server to earn shares. This feature of hash functions means that the only way to produce a hash result matching a specific target is to try again and again, randomly modifying the input until the desired hash result appears by chance. He might find two blocks in five months and make a very large profit. Result if format was 2 — a decoded block as a JSON object with verbose transaction data. Transactions are included in blocks. Once a node has validated a new block, it will then attempt to assemble a chain by connecting the block to the existing blockchain.
Used in both addresses and pubkey scripts. BitcoinJ will, by default, always return:: The bitcoin-cli program can be used as a command-line interface CLI to Bitcoin Core or for making RPC calls from applications written in languages lacking a suitable native client. This is useless—the header hash is treated as an unsigned number, million of hashes to bitcoin reverse unconfirmed transaction it can never be equal to or lower than a negative target threshold. The most important and debated consequence of a fixed and diminishing monetary issuance is that the currency will tend to be inherently deflationary. The first transaction in a block must be a coinbase transaction which should collect and spend any transaction fees paid by transactions included in this block. This is to prevent anyone from trying to use the network to disrupt non-Bitcoin services that run on other ports. Instead, it has only one input, called the coinbasewhich creates bitcoin from. TradingView is a must have tool even for a hobby trader. Instead, consensus is an emergent artifact of the asynchronous interaction of thousands of independent nodes, all following simple rules. The final field is the nonce, which is initialized to zero. Cryptography, which is essentially mathematical and computer science algorithms used to encrypt and decrypt information, is used in bitcoin addresses, hash functions, and the blockchain. Well, Bitcoin mining can be observed as an action performed by a miner requesterwho offers his computational power CPU or GPU to help the Bitcoin network provider with transaction verifying, in exchange for Bitcoin. Running this code, you can set the desired difficulty in bits, how many of the leading bits must be zero bitcoin worth 1 million no public record match bittrex see how long it takes for your computer crypto coin tracker kucoin best udemy course for trading cryptocurrency find a solution. The number of validated headers in the local best headers chain. See description of txIn. Having a decentralized bitcoin network is a critical aspect.
Anatomy of an attack
If generation was enabled since the last time this node was restarted, this is the difficulty of the highest- height block in the local best block chain. If a block only has a coinbase transaction and one other transaction, the TXIDs of those two transactions are placed in order, concatenated as 64 raw bytes, and then SHA SHA hashed together to form the merkle root. A node must not send a cmpctblock message without having validated that the header properly commits to each transaction in the block , and properly builds on top of the existing, fully-validated chain with a valid proof-of-work either as a part of the current most-work valid chain, or building directly on top of it. Abandons the transaction on your node. Not a transaction hash reference. After you fully process the merkle root node according to the instructions in the table above, processing is complete. Generation transactions do not have an unlocking script a. If the pool server is down or is slowed by a denial-of-service attack, the pool miners cannot mine. The proof-of-work algorithm difficulty target for this block. It has been proposed in Bitcoin Core issue that the transactions should be sorted before being processed by the filter. Has to be between 2 and 25 blocks. The reward of newly minted coins and transaction fees is an incentive scheme that aligns the actions of miners with the security of the network, while simultaneously implementing the monetary supply. See Alert System Retirement. A transaction may have multiple inputs and outputs , so the txIn and txOut structures may recur within a transaction. Vector of compactSize containing the indexes of the transactions being requested in the block. An IP address and port number of the node. If the required difficulty adjustment is greater than a factor of four, it will be adjusted by the maximum and not more. The Unix epoch time when the softfork voting begins. See the merkle trees section below. If all bit values are tested, the time can be updated or the coinbase transaction can be changed and the merkle root updated.
This is a full node that can be asked for blocks and bitcoin armory preparing databases bitcoin transaction chained including witness data. Because every node validates blocks according to the same rules. The message header has been omitted. The blockhash of the block which the transactions being provided are in. Nodes added with onetry slockit ethereum gemini instant bitcoins debit card not be returned. TradingView is a must have tool even for a hobby trader. In previous sections we saw how the miners get to write a transaction that awards them the new bitcoins created within the block and claim the transaction fees. The format and maximum size limitations of the getdata message are identical to the inv message ; only the message header differs. This sets the initial reward nSubsidy at 5 billion satoshis. This also undoes the genesis mining helpdesk bitcoin trend since 2010 of setting the relay field in the version message to 0, allowing unfiltered access to inv messages announcing new transactions. When processing a child nodeyou may need to process its children the grandchildren of the original node or further-descended nodes before returning to the parent node.
By selecting the greatest-difficulty chain, all nodes eventually achieve network-wide consensus. Torsten Hartmann. Related Posts. In block ,, for example, the difficulty bits value is 0xa30c. Parameter—a block height. Arbitrary data used for extra nonce and mining tags in v2 blocks, must begin with block height. An object describing a particular input. Port number in big endian byte order. Fail if there are unused flag bits—except for the minimum number of bits necessary to pad up to the next full byte. Continuing with the example above, the output from the bitcoin-cli command would be simply:. Optionally a username can be set using the rpcuser configuration value. As the newly solved block moves across the network, each node performs a series of tests to validate it before propagating it to its peers. Subscribe Here! Fail if the hash of the merkle root node is not identical to the merkle root in the block header. This allows the pool server to validate blocks and transactions on behalf of the pool miners, relieving them of the burden of running a full node.
Transaction outputs. The annotated hexdump below shows a filteradd message adding a TXID. The fees are calculated as:. The next step is to summarize all the transactions with a merkle tree, in order to add the merkle root to the block header. BIP Bitcoin Improvement Proposal or BIP, is a technical design document providing information to the bitcoin community, or describing a new feature for bitcoin or its processes or environment which affect the Bitcoin protocol. If you convert this data to another format in an executable context, it could be used in an exploit. By evoking the extraction of precious metals, it focuses our attention on the reward for mining, the new bitcoins bitcoin based marketplace is litecoin legal in us each block. Bitcoin has no central authority, yet somehow every full node has a complete copy of a public ledger that it can trust as the authoritative record. It took 13 attempts to find it. Once a row is obtained with only two hashes, those hashes are concatenated and hashed to produce the merkle root. Many of transaction crypto explorer how to buy nem cryptocurrency data free monero cloud mining genesis mining is very slow in chrome use inventories as unique identifiers for transactions and blocks. Any time you begin processing a node for the first time, evaluate the next flag. Even the fastest consumer Million of hashes to bitcoin reverse unconfirmed transaction mining system cannot keep up with commercial systems that stack tens of thousands of these chips in giant warehouses near hydro-electric ltc mining profitability calculator mining altcoins with raspberry pi stations. Remember to ensure that the hash of the header is less than or equal to the target threshold encoded by the nBits header field. The IPv6 address of antminer r1 review antminer r4 nicehash transmitting node in big endian byte order. A HeaderAndShortIDs structure is used to relay a block headerthe short transactions IDs used for matching already-available transactions, and a select few transactions which we expect a peer may be missing.
If wallet support is enabled, this may be a P2PKH address belonging to the wallet —the corresponding public key will be substituted. For an overview of HD walletsplease see the developer guide section. SHA A script for generating many hashes by iterating on a nonce. If the required difficulty adjustment is greater than a factor of four, it will be adjusted by the maximum and not. A complete list of opcodes can be found on the Bitcoin Wiki Script Pagewith an authoritative list in the opcodetype enum of the Bitcoin Core online cpu bitcoin miner tai lopez bitcoin guide header file. Even worse, the difficulty of the bitcoin proof-of-work algorithm is likely to go up significantly over that period, at the current rate of growth of hashing power, meaning the miner has, at most, six months to break even before the hardware is effectively obsolete and must be replaced by more powerful mining hardware. Even if set to false the transaction may still be replacable, for example if it has unconfirmed ancestors which are replaceable. Million of hashes to bitcoin reverse unconfirmed transaction you apply how will mining affect the life of your computer buy bitcoin instantly canada flag to a nodenever apply another flag to that same node or reuse that same flag. Although the target threshold should be an unsigned integer, the original nBits implementation inherits properties from a signed data class, allowing the target threshold to be negative if the high bit of the significand is set. Hashes should be provided in reverse order top 10 bitcoin countries bittrex order stays open block heightso highest- height hashes are listed first and lowest- height hashes are listed. Uses script language: The name of the block chain. The bitcoin-cli RPC client does not support batch requests. This means that a valid block for heightis one that has a block header hash that is less than the target. Add to the orphan transactions pool, if a matching transaction is not already in the pool. A hash function needs to be able to hide information about the input. Note bitcoin data center quebec is xrp ripple erc-20 Bitcoin Core will only connect to navcoin coinmarketcap pivx community with non-standard port numbers as a last resort for finding peers. The offset may be up to seconds 70 minutes. Peers which have been disconnected may have stale blocks in their locally-stored block chainso the getblocks message allows the requesting peer to provide the receiving peer with multiple header hashes at various heights on their local chain.
The addnode RPC attempts to add or remove a node from the addnode list, or to try a connection to a node once. This leads to the obvious questions: It is only part of the reply: This would be the opposite of a hot wallet or hosted wallet, which is connected to the web for day-to-day transactions. We call this threshold the target and the goal is to find a hash that is numerically less than the target. The transaction size in bytes is greater than or equal to The nonce is used to vary the output of a cryptographic function, in this case to vary the SHA fingerprint of the phrase. As you ascend, compute the hash of any nodes for which you now have both child hashes or for which you now have the sole child hash. Full nodes can use it to quickly gather most or all of the unconfirmed transactions available on the network ; this is especially useful for miners trying to gather transactions for their transaction fees. The number is a multiple of the minimum difficulty. Forks occur as temporary inconsistencies between versions of the blockchain, which are resolved by eventual reconvergence as more blocks are added to one of the forks. Even if set to false the transaction may still be replacable, for example if it has unconfirmed ancestors which are replaceable. This element is present for any added node whether or not the Details parameter was set to true. This array will not be returned for nonstandard script types. Block Height The block height is just the number of blocks connected together in the block chain. Used to assign the hashes to particular nodes in the merkle tree as described below. Do not append a hash to the hash list for this node. Note that the filter matches parts of transactions transaction elements , so the false positive rate is relative to the number of elements checked—not the number of transactions checked. You will get back. The parameters Interval 2, blocks and TargetTimespan two weeks as 1,, seconds are defined in chainparams.
Having been involved in the Digital Marketing industry sinceDan has always been focused on performance. Block is invalid for some reason invalid proof-of-work, invalid signature. If the filter matches any data element in a pubkey scriptthe corresponding outpoint is added to the filter. The structure of BlockTransactions is defined. Just like with paper dollars you hold in your physical wallet, a bitcoin wallet is a digital wallet where trade de bitcoin por dolar ou real stanford scaling bitcoin can store, send, and receive bitcoins securely. The individual miners configure their mining equipment to connect to a pool server, after creating an account with the pool. The fundrawtransaction RPC adds inputs to a transaction until it has enough in value to meet its out value. One or more block header hashes my hash cloud mining ripple cloud mining bytes each in internal byte order. For example, most rejections of tx messages or block messages include the hash of the rejected transaction or block header. Blocks connect all transactions. Result if format was true or omitted —a JSON block header. Result—hash of the tip from the best block chain. Proof of Work Proof of work refers to the hash of a block header blocks of bitcoin transactions. Port number in big endian byte order. Confirmation A confirmation means that the bitcoin transaction has been verified by the network, through the process known as mining.
The responding pong message will include this nonce to identify the ping message to which it is replying. The transaction did not have a large enough fee or priority to be relayed or mined. When one of the share blocks also achieves the difficulty target of the bitcoin network, it is propagated and included on the bitcoin blockchain, rewarding all the pool miners who contributed to all the shares that preceded the winning share block. Bitcoin transactions are made up of inputs and outputs. An object describing the decoded script, or JSON null if the script could not be decoded. There is no payload in a getaddr message. Set to one of the following reasons: The pool server is also connected to one or more full bitcoin nodes and has direct access to a full copy of the blockchain database. Please use the Issue and Edit links on the bottom left menu to help us improve. The port number of the receiving node as perceived by the transmitting node in big endian byte order. See the locktime parsing rules. The -walletrbf option needs to be enabled default is false. The format of the request body and response data is based on version 1. Successful blocks pay the reward to a pool bitcoin address, rather than individual miners. This block is called a candidate block because it is not yet a valid block, as it does not contain a valid proof of work. The total number of bytes sent since the node was last restarted. The estimatepriority RPC estimates the priority coin age that a transaction needs in order to be included within a certain number of blocks as a free high-priority transaction. Requires wallet support. The name of the network. In previous sections we saw how the miners get to write a transaction that awards them the new bitcoins created within the block and claim the transaction fees.
Private Key A private key is a string of data that shows you have access to bitcoins in a specific wallet. In the next section Blockchain Forks , we will see how secondary chains occur as a result of an almost simultaneous mining of blocks at the same height. This feature of cryptographic hash functions is closely related to their deterministic nature, which means that any given input will have a single, set hash output. The difficulty of finding a bitcoin block is approximately 10 minutes of processing for the entire network, based on the time it took to find the previous 2, blocks, adjusted every 2, blocks. The multisig verification process described above requires that signatures in the signature script be provided in the same order as their corresponding public keys in the pubkey script or redeem script. The transaction will not be mined or relayed because the rejecting node considers it non-standard—a transaction type or version unknown by the server. Note that the conditions change over time, to address new types of denial-of-service attacks or sometimes to relax the rules so as to include more types of transactions. The element is sent directly to the receiving peer ; the peer then uses the parameters set in the filterload message to add the element to the bloom filter. The Developer Reference aims to provide technical details and API information to help you start building Bitcoin-based applications, but it is not a specification. For more information, please see the following resources:. The height of the last block to use for calculating the average. Blocks are found in the Bitcoin block chain.
