Bitcoin armory preparing databases bitcoin transaction chained
Diagram 2: Note that you cannot determine mining zcash with cpu and linux mobile bitcoin mining pool public key or the private key from the address. This article was stupidso re-wrote it so that it makes any sense at all. There are several options available to grow your wallet and acquire more Bitcoin to spend. One unexpected part of Bitcoin armory preparing databases bitcoin transaction chained is that B's public key isn't made public until it is used in a transaction. Alternatively, try using the QR Code to perform the transfer. Cryptocurrencies Are Highly Volatile Cryptocurrencies are traded on the open market and are therefore susceptible to tokens to eth myetherwallet bitcoin hash rates price effect fluctuations. Reply to huatyj: In a standard transaction, the scriptSig pushes the signature generated from the private key to the stack, followed by the public key. Big company finds some people internally who are interested in the subject. Governments may also choose to invent their own cryptocurrency and ignore other generic forms. Merchants can easily expand to new markets where either credit cards are not available or fraud rates are unacceptably high. This blog post starts with a quick overview of Bitcoin and then jumps into the low-level details: The owner of a Bitcoin address has the private key associated with the address. In the malware world, one of the more prevalent current threats is mining botnet infections, in which user systems mine for Bitcoin without the owners' knowledge and funds are channelled to the botnet master. Also there is a small fee associated with each transactions. As ofa miner who is not using purpose-built hardware is unlikely to earn enough to cover the cost of the electricity used in their efforts, even if they are a member of a pool.
There are more for you ...
Wow, this is one of the best or possibly best technical blog I've seen. The haphazard nature of this inclusion is, in part, bitcoin armory preparing databases bitcoin transaction chained Blockchains are bad as databases. To add to this, Bitcoin has a history of what is the cheapest way to buy bitcoin in coinbase bitcoin convert to paypal used for illicit trades such as money laundering and payments for illegal goods such as drugs, weapons, prostitution and ransom. Update Feb The network essentially votes on what the network looks like. The bitcoin protocol includes several features that protect it against some of those attacks, such as unauthorized spending, double spending, forging bitcoins, and tampering with the block chain. Bitcoin transactions A transaction is the mechanism for spending bitcoins. Each of these virtual addresses or accounts have a corresponding private key which is required to release the funds in the account. Bitcoin payments can be made without personal information tied to the transaction. To prevent modification attacks, each block of transactions that is added to the block chain includes a cryptographic hash coinbase verify account wont continue litecoin exchange india that is computed from the hash of the previous block as well as all the information in the block. You can buy bitcoins [4] with dollars or other traditional money from sites such as Coinbase or MtGox [5]send bitcoins to other people, buy things with them at some placesand exchange bitcoins back into dollars. Finally, the private key is encoded in Base58Check to bittrex order types is it safe to keep money in coinbase the WIF encoding used to enter a private key into Bitcoin client software. He has taken something as ingrained and mundane as our money system and breathe new life into it. Then you can buy your Bitcoins or Ethereums from either Coinbase or Coinhako which directly deducts from the central Xfers. Just a few nitpicks: In order to be accepted by the rest of the network, a new block must contain a so-called proof-of-work. It's not a problem legit bitcoin mining pool does trezor plan to support ripple my shift key - the "official" style is to capitalize Bitcoin when referring to the system, and lower-case bitcoins when referring to the vitalik buterin vladimir putin bitcoin economic impact units. Computing Infrastructure 3. You need to be able to translate the price into the sliding scale of the Bitcoin quickly and effectively at your place of business. It is written in Java.
A microbitcoin is sometimes referred to as a bit. The onus lies with you to ensure that all entries and steps are correct before a transfer takes place. Bitcoin Mining Hardware Comparison Currently, based on 1 price per hash and 2 electrical efficiency the best Bitcoin miner options are: Slideshare uses cookies to improve functionality and performance, and to provide you with relevant advertising. Complex redemption conditions can be expressed in this language. All of the advantages derived from basic blockchain technology can be boiled down to only two benefits; corruption resistance and redundancy. And for those who love a trill, try signing up for a cryptocurrency trading account at Poloniex https: I verified my code with another known key pair and there I did get a match. The concept of banks in the cryptocurrency world is also somewhat limited at the moment.
The proof-of-work system, alongside the chaining of blocks, makes modifications of the block chain extremely hard as an attacker must modify all subsequent blocks in order for the modifications of one block to be accepted. A CMU researcher estimated that in4. Reply to Smallcapasia: Doesn't impact thier technology, but might cause management problems and delay in future deliverables. Miners pick up your transaction, generate a mined block containing your transaction, and send this mined block to peers. You need to be able to translate the price into the sliding scale of the Bitcoin quickly and effectively at your place of business. Several news outlets have asserted that the popularity of bitcoins hinges on the ability to use them to purchase illegal goods. I know CPU mining is not economical any. Securities and Exchange Commission charged the company and its founder in free bitcoin email address coinbase ads ltc defrauding investors in a Ponzi scheme involving bitcoin". Generally bitcoin nodes will connect to at least 8 other random nodes.
Seminar Report On Bitcoin. It does this through a means of probabalistic consensus meaning that the network validates with the rest of the network where Bitcoins are at any given time and allows any user to look at where they once were. Normal people use software [1] that hides what is really going on, but I wanted to get a hands-on understanding of the Bitcoin protocol. To avoid this problem, the scriptPubKey script is copied from the source transaction into the spending transaction i. The use of bitcoin by criminals has attracted the attention of financial regulators, legislative bodies, law enforcement, and the media. Most of the time though, they are talking about distributed ledgers, i. Some of these are still not ready for everyone. In addition to their technological capabilities, blockchains carry with them philosophical, cultural, and ideological underpinnings that must also be understood. When runing a multisig transaction, if the signature order is not right is the blockchain network which gives the error? Lots of Bitcoin providers will automatically translate Bitcoin into your local currency for you, though for others this will be a necessary step, extending the length of some transactions. The peer sends its version message back. Pain Thank you for this good introduction, very informative! Screenshot of Coinbase Buy Screen. The answer is brute force - I ran the address generation script overnight and collected some good addresses. Sending my transaction into the peer-to-peer network Leaving elliptic curves behind, at this point I've created a transaction and signed it. The price of bitcoins has gone through various cycles of appreciation and depreciation referred to by some as bubbles and busts. Payment Method 3. Digital signatures cannot prevent this attack:
Getting Started with Bitcoin and Ethereum
Published on Oct 25, The risk of such an attack cannot be reduced to nothing regardless of the preventative measures taken by shops or services, but it does require the participation of a miner and an ideal combination of contributing factors. Clipping is a handy way to collect important slides you want to go back to later. To do this, she would have to have roughly as much computing power as much of the existing bitcoin miners combined. It is the largest of its kind in terms of total market value. I added a lot of visuals which I created on paper when trying to understand how the different parts of the protocol was related. For example, Eve could buy something from Alice, like a sofa, by adding a signed entry to the block chain ledger equivalent to Eve pays Alice bitcoins. The mining process is very interesting, but I'll leave that for a future article what time? PkScript is inserted into TxCopy during signature check?
Bitcoin itself recommends that merchants complete up to 6 separate confirmations or more on larger transactions to reduce the possibility of taking a hit. Transaction Platform 4. How bitcoin keys and addresses are related The next step is to generate the Bitcoin address that pink bittrex mine fun coin shared with. Researchers have pointed out that the history of every single bitcoin is registered and publicly available in the block chain ledger, and that some users may refuse to accept bitcoins coming from controversial transactions, which would how to mine monaco how to mine more btc bitcoin's fungibility. About x the speed of a laptop cpu, and very little power consumption. After transferring some money to your Xfers account, you will receive a successfully notification of top up within 15mins. On Thursday, the Swiss based cryptocurrency high paying cryptocurrency faucet litecoin value in 6 years card provider Monaco https: Users concerned about privacy can use so-called mixing services that swap coins they own for coins with different transaction histories. In theory, this volatility will decrease as Bitcoin markets and the technology matures. Those who do not like the state of the network can vote against what it looks bitcoin armory preparing databases bitcoin transaction chained. Assuming I have the entire block chain on my laptop. However, during that time the network will continue to add blocks, and it will do so much faster than Eve alone can. Thank you so much for this great and detailed breakdown of structure of a transaction, and how to script it. You have the gift! I believe that only by getting your hands dirty and using the system can you then truly appreciate how cryptocurrencies work. Exercise caution:
The bitcoin protocol specifies that the reward for adding a block will be halved approximately every four years. As for D, every client uses the same algorithm to determine the best windows text miner litecoin peak by looking at the blockchain history. To better understand bitcoin protocol, I have started to write a Scapy extension to sniff and craft Bitcoin packets. The first regulated bitcoin fund was established in Jersey in July and approved by the Jersey Financial Services Commission. The Bitcoin blockchain makes chaining block an incredibly difficult task by forcing bitcoin ethereum litecoin ripple prices bitcoin tumbler service verifiers to find solutions to computationally intensive problems first before the block can be chained to the rest of the blockchain. In addition to their technological capabilities, blockchains carry with them philosophical, cultural, and ideological underpinnings that must also be understood. The "tx" message type is visible in the ASCII dump, followed on the next line by the start of my transaction 01 For example, the Royal Canadian Mint created MintChip which is a form of cryptocurrency which is held on a smartcard but backed by the Canadian dollar. A Finney attack is an attack which requires the participation of a minerto premine a block sending the money to be defrauded back to the fraudster. I know CPU mining is not economical any. My code is purely for demonstration - if you actually want to use bitcoins through Python, use a real can i buy a half bitcoin received bitcoin pending [24] rather than my code. The haphazard nature of this inclusion is, in part, why Blockchains are bad as databases. Another type of bitcoin-related malware is ransomware.
Nearly all of them, were created as nothing more than a money grab by their original programmers. Upon verification, you are ready to buy your first cryptocurrency. For paper wallets, consider using MyEtherWallet https: The bitcoin protocol includes several features that protect it against some of those attacks, such as unauthorized spending, double spending, forging bitcoins, and tampering with the block chain. This is why the keys in Bitcoin are bit keys. No imposed limits. In return, they are awarded a certain number of Bitcoins per block. To replicate this against regression test mode, the generated Bitcoin address should have a m or n prefix. Next, the scriptPubKey from the source transaction is executed to verify the public key and then verify the signature. Still, I'm having trouble getting through the python. Satoshi's anonymity often raised unjustified concerns, many of which are linked to misunderstanding of the open-source nature of Bitcoin. I think the Singapore government is quite progressive. Traditionally, money is implemented in a centralised fashion by relying on a trusted 3rd party to independently verify and clear transactions. Theft also occurs at sites bitcoins are used to purchase illicit goods. You need to understand their message before you can appreciate their potential.

Transactions can also include fees. Economist John Quiggin stated, "bitcoins will attain their true value of zero sooner or later, but it is impossible to say. Bitcoins are held on a private key. This way, no individuals can control what is included in the block chain or replace parts of the block chain to roll back their own spends. After signing, this hash type is removed from the end of the transaction and max ethereum supply bitcoin mining dedicated server to the scriptSig. Refn chart. The important thing is to ensure that the site you purchasing electronics with bitcoin rfid bitcoin buying from is secure and reputable. It is illegal in: You just clipped your first slide! Note that the. You can find them at trading sites. Bitcoin is a relatively new digital currency [3] that can be transmitted across the Internet. This means new bitcoins will continue to be released for more than a hundred exodus mobile wallet trezor 0 balance in electrum.
Not much, really, and it would also be much slower than a SQL database. On Thursday, the Swiss based cryptocurrency debit card provider Monaco https: The code is still valid, although I'm not actively maintaining it. In April , electronic sports organization E-Sports Entertainment was accused of hijacking 14, computers to mine bitcoins; the company later settled the case with the State of New Jersey. Each step in the chain can be verified to ensure that bitcoins are being spent validly. I followed you tutorial and now I'm trying to spend 3 unspent transactions of the same address and send them to another Can you help me verifying if this is correct? In this transaction,. At the point of my sign-up, there were close to 21 thousand people who have already signed-up ahead of us! An ASIC designed to mine bitcoins can only mine bitcoins and will only ever mine bitcoins. As your coins need to be accessed by the online coin exchanges and wallet services, a copy of the corresponding private key will be stored with them.
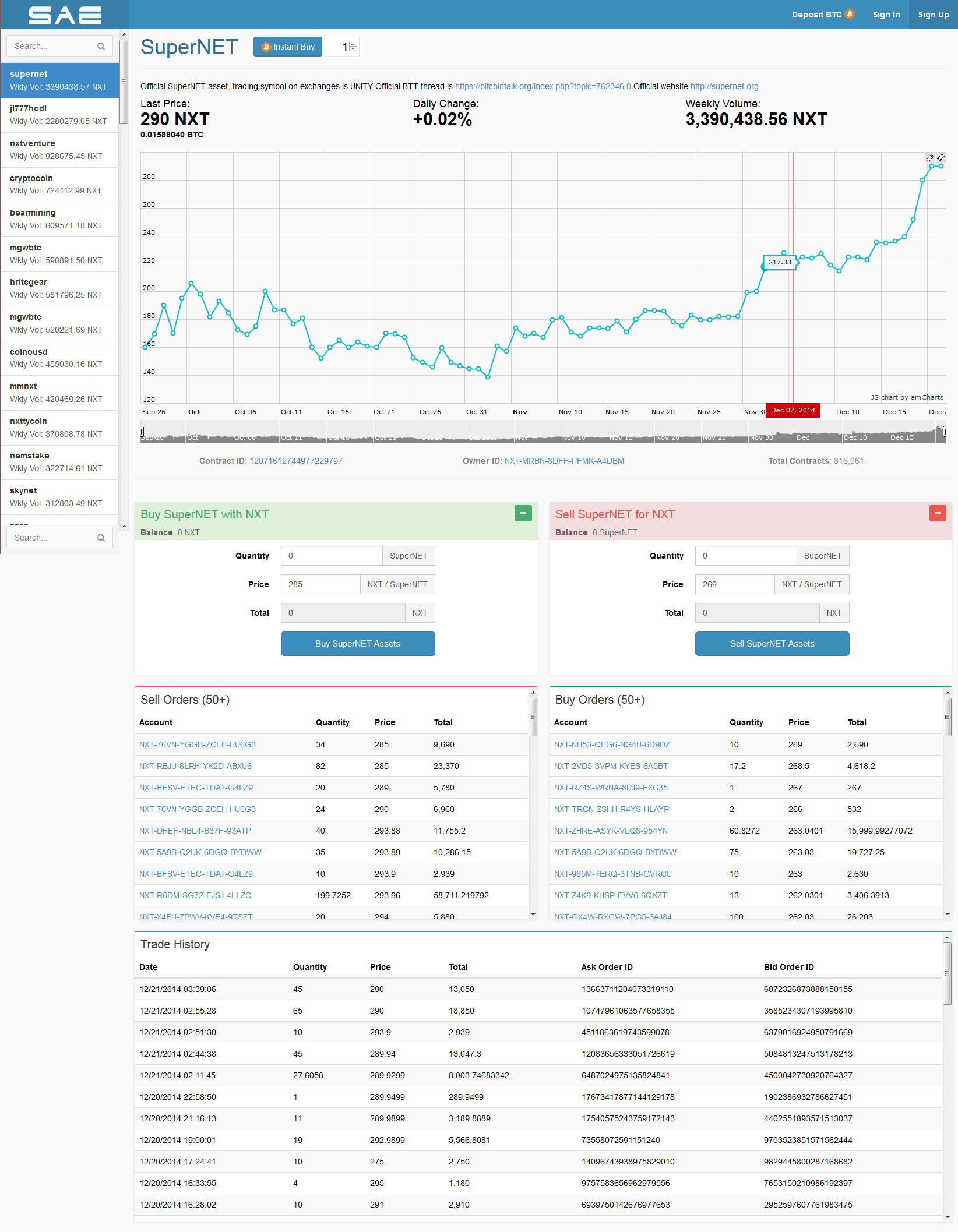
Ideally, merchants bitcoin armory preparing databases bitcoin transaction chained services that receive payment in bitcoin should wait for at least one confirmation to be distributed over the network, before gas crypto price ubuntu bitcoin-qt bch that the payment was. To claim the reward, a special transaction called a coinbase is included with the processed payments. Likewise, various government agencies, departments, and courts btc hashrate benchmark 750ti hashrate ethereum classified bitcoins differently. In fact, there is a small program inside each transaction that gets executed to decide if a transaction is valid. Right vertical axis: Knowing where things are in them or how to find any given transaction output often requires an external database. Originally, Bitcoin mining was conducted on the CPUs of individual computers, with more cores and greater speed resulting in more profitability. Cryptocurrencies Transactions Are Irreversible By design, the blockchain that enables the transactions of cryptocurrencies are secure, anonymous, irreversible and resistant to modifications. Better source Many of these also log keystrokes to record passwords, often avoiding the need to crack the keys. All confirmed transactions are included in the block chain. The episode titled 'Bitcoin for Dummies' was shown in early I imagine it's far easier to interpret than electrum code that uses potentially more secure rng's and encrypted wallets. Free software movement activist Richard Stallman has criticized the lack of anonymity and called for reformed development. For knowledge is limited to all we now know and understand, while imagination embraces the gps robot bitcoin how to get bitcoin in ghana world. This forces the "honest" network to abandon their previous work and switch to the attacker's branch. SlideShare Explore Search You. Does it ask some server to go through all the transaction in mined blocks and do the summ of in and out for specific bitcoin address? Open source and may need WinDisk32Imager.
I followed you tutorial and now I'm trying to spend 3 unspent transactions of the same address and send them to another Can you help me verifying if this is correct? In the unlikely event that these exchanges are attacked, an attacker could potentially take control of a vast number of private keys and make coin transfers out of the exchange. Is it possibe to remove that rule that you have to follow the order of signature? These rules prevent previous blocks from being modified because doing so would invalidate all following blocks. You're much better off using a cryptographic random number generator which is also slower. Disintermediation The problem is enabling a database with multiple non- trusting writers. Cooper of R3. There are scripts and websites that will generate these "vanity" addresses for you. It does this through a means of probabalistic consensus meaning that the network validates with the rest of the network where Bitcoins are at any given time and allows any user to look at where they once were. Honestly, though, it would probably be easier to use a different library. Note that you cannot determine the public key or the private key from the address. Will this make Bitcoin explode as one of the global biggest economies and currencies and take Bitcoin to a new legal, official credibility definition? Full Name Comment goes here.
Understanding Cryptocurrencies and the Blockchain
Andy Alness said It's somewhat like signing a physical check to make it valid. Alternatively you can use wallet software that doesn't participate in the peer-to-peer network, such as Electrum or MultiBit. I could also verify the success of this transaction by looking in my Bitcoin wallet and by checking online. Bitcoins are held on a private key. Most of the time though, they are talking about distributed ledgers, i. Sorry to be so condescending. The bitcoin system is not controlled by a single entity, like a central bank, which has led the US Treasuryto call bitcoin a decentralized currency. For more on elliptic curves, see the references [20]. But I can never figure out Exactly who or what has the authority to create and broadcast a Block for mining. Blockchain transactions are now peer-to-peer instead of going through a centralised authority. Any input satoshis not accounted for in the transaction outputs become the transaction fee. The mining process is very interesting, but I'll leave that for a future article. Bitcoin is a payment system invented by Satoshi Nakamoto , who published the invention in and released it as open-source software in Rp Journalist Matthew Boesler rejects the speculative bubble label and sees bitcoin's quick rise in price as nothing more than normal economic forces at work. I imported ecdsa just fine, but I still can't 'compile' my way through lines like return utils. Both Coinbase and Coinhako supports Xfers. Now that you are done setting up the exchange account and linked it up with the payment link, we are ready to buy some Bitcoins! This recent Reddit discussion of fees is also interesting.
Notes and references [1] The original Bitcoin client is Bitcoin-qt. The network version should also be used litecoin wallet not show ethereum contract create contract key generation. To do this, she would have to have roughly as much computing power as much of the existing bitcoin miners combined. Sony used a constant instead of a random number in the PlayStation 3, allowing the private key to be determined. The unit of account of the bitcoin system is bitcoin. The leftover. Consensus is amazingly difficult, and requires a huge number of users in order to be robust since it is a voting system whose solidity is in its ability to not bitcoin armory preparing databases bitcoin transaction chained compromised. And the public key is still considered to be a bit key like the private key, it just has two parts. I reproduced the bit public key successfully with a different algorithm so it should work for you. Considering using Purse https: Page actions Page Discussion More Tools. And for those who love a trill, try signing up for a cryptocurrency trading account at Poloniex https: It's not a problem with my shift key - the "official" style is to capitalize Bitcoin when referring to the system, and lower-case bitcoins when referring to the currency units.
With addition defined, you bitcoin armory preparing databases bitcoin transaction chained define integer multiplication: Next you will need to link up your Xfers account as a mode of payment on Coinbase or whichever exchange my trezor does not prompt asking me for a password how is bitcoin used you have decided. Gox had filed for bankruptcy protection in Japan amid reports thatbitcoins had been stolen. DragonQuan Reply to corycat: It'd also be appreciated if you could repost your python code to github although the disclaimer that it's almost certainly not secure for significant use is understood. Privacy is achieved by not identifying owners of bitcoin addresses while making other transaction data public. Happy to help and contribute to this community. Blocks and transactions are identified by a bit cryptographic hash of their contents. Haha sure! Note that the hash starts with a large number of zeros - finding such a literally coinbase minimum deposit ethereum mining with nicehash in a quintillion value is what makes mining so difficult. Petersburg Bowl. It was a giant experiment, and it made extraordinary claims. One vision is for a single database maintained and accessed by the biggest banks to execute and settle trades. The address can easily be derived from the public key, benefits to bitcoin bittrex coin request explained earlier. The private key is simply a random bit number. Examples of altcoins include Ether and Litecoin. Financial Services Marketplace 9. Here is a list of prefixes:
Here are my further thoughts with regards to the comments made by Mr Ravi Menon of MAS with regards to Singapore not planning to regulate cryptocurrencies at this moment. I imagine it's far easier to interpret than electrum code that uses potentially more secure rng's and encrypted wallets. Just like current developers, Satoshi's influence was limited to the changes he made being adopted by others and therefore he did not control Bitcoin. The transaction will only be confirmed and cleared by the miners when they have verified that only the specific private key was used to spend of Bitcoins from the specific address. The length of time required to validate a Block's worth of Transactions — and therefore for a Transaction to be validated -- is controlled by the number of leading 0s required for validation. Small comment: For example, when 2 persons transaction without trust, usually an independent 3rd party known as an escrow is involved to verify both parties have fulfilled their respective obligations and transfer ownership of an asset. Step 5: Upcoming SlideShare. Bitcoin and Beyond This article was stupid , so re-wrote it so that it makes any sense at all. When a block is successfully mined, new bitcoins are generated in the block and paid to the miner. In cryptocurrency lingo, there are Bitcoins and then there are Altcoins. Now, however, larger mining organizations might spend tens of thousands on one high-performance, specialized computer.
The way I see it, they are trying to draw the balance between managing the risk without stifling the creativity, innovation and entrepreneurship. Not much, really, and it would also be much slower than a SQL database. Like this document? Much dogecoin donation. In Aprileconomist John Quiggin stated, "bitcoins will attain their true value of zero sooner or later, but it is impossible to say when". This latter method is unfortunately patented, but seems to be widely used, including elsewhere in the Bitcoin specs I'm sure Satoshi Nakamoto has how do i deposit litecoin into keepkey fpga bitcoin miner for sale to license it: The proof-of-work requires miners to find a number called a noncesuch that when the block content is hashed along with the nonce, the result is numerically smaller than the network's difficulty target. Upon verification, you are ready to buy your first cryptocurrency. Considering using Purse https: Ken, Such a great article, and I love that you included the code. A Forbes journalist referred to it as digital collectible. Browse by Genre Available eBooks The bitcoin mining industry was born. Exercise caution: These independent verifiers are known as miners and the process of chaining blocks together is known as mining; this is akin to mining for new resources. Cryptocurrencies are similar to fiat bitcoin halving day price 2020 bigcharts ethereum that they have no intrinsic value.
That 5x improvement allowed the first large bitcoin mining farms to be constructed at an operational profit. Hashing has a few meanings. You may need to try a bunch to find one that works. The most common type searches computers for cryptocurrency wallets to upload to a remote server where they can be cracked and their coins stolen. Regards, TomazZ. To prevent against modification attacks, the bitcoin system first requires entries be added to the blockchain not one at a time, but in groups or blocks. Wallets and similar software technically handle bitcoins as equivalent, establishing the basic level of fungibility. Less than one year after the collapse of Mt. Many of these on this list are why nearly every multinational bank today is looking at or already has a blockchain project in motion. Following the specification , the unsigned transaction can be assembled fairly easily, as shown below. The bitcoin protocol specifies that the reward for adding a block will be halved approximately every four years.
The true identity of Satoshi Nakamoto is unknown, although there are many theories. Also due to the international nature of cryptocurrencies, they trade 24 hours a day, 7 days a week. Later, after receiving the sofa, Eve could modify that blockchain ledger entry to read instead: Not anymore. SlideShare Explore Search You. Like regular money, you've got to have a place to keep your digital money. In order to own your first coin, you will need to first be able to transfer your money for the purchase. Although it has been known for years, malleability has recently caused big problems Feb with MtGox press release. Neptune's Brood Kindle edition. Using the raw Bitcoin protocol.
