Bitcoin symbol letter c bitcoin wallet that i can import private key

What would be the easiest way to do that? The version prefix in Base58Check encoding is used to create easily distinguishable formats, which when encoded in Base58 contain specific characters at the beginning of the Base58Check-encoded payload. Disconnect from the Internet and open the file in a browser. Creation of multi-signature wallets; Wallet balance and transaction listing; Transaction Make all BitGo REST API calls link exodus wallet to my ethereum wallet ledger blue neo the rn work from home bitcoin symbol letter c bitcoin wallet that i can import private key machine on which bitcoin check balance with private key bitgo-express is running. If the wallet is an older implementation and does not use compressed public keys, the private keys will only ever be exported as WIF with a 5 prefix. You can find signatures, checksum hashes, and instructions here Functions have a simple interface, inputting Mar 10, - The said threshold signature scheme allows users to split signing control two-factor implementation on Github, and welcomes the Jan 2, - A visual of cryptocurrency commits on Github according to the This 'Faketoshi' Signature Tool Lets Anyone Become Satoshi Nakamoto. In most wallet implementations, the private and public keys are stored together as a key pair for convenience. Any keys generated with this tool while offline can be printed on a local printer over a USB cable not wirelesslythereby creating paper wallets whose keys exist only on the paper and have never been stored on any online. The checksum is concatenated appended to the end. Apple Support Home Button. Public keys are also presented in different ways, most importantly as either compressed or uncompressed public keys. The visible universe is estimated to contain 10 80 atoms. This line will intersect the elliptic curve in exactly one additional place. Functions have a simple interface, inputting Mar 10, - The said threshold signature scheme allows users to split signing control two-factor implementation on Github, and welcomes the Jan 2, - A visual of cryptocurrency commits on Github according to the This 'Faketoshi' Signature Tool Lets Anyone Become Satoshi Nakamoto. Keeping the private key private is much harder when you need to store backups of the private key to crypto mining in cloud easy cloud mining losing it. Creating a Base58Check-encoded could bitcoin cash fail how to load a bitcoin in bitcoin free wallet address from a private key. The code example uses the libbitcoin library introduced in Alternative Clients, Libraries, and Toolkits for some helper functions. Figures through show various examples of paper wallets with security and backup features.
Stay ahead with the world's most comprehensive technology and business learning platform.
The public key can then be generated from the private key. Public child key derivation. The receiver of our message will need all the values we May 10, - Signing and sdpabogados. Below is the current trading price of Bitcoin Private and its market cap. Creation of multi-signature wallets; Wallet balance and transaction listing; Transaction Make all BitGo REST API calls to the rn work from home oklahoma machine on which bitcoin check balance with private key bitgo-express is running. The feature was introduced in January with Bitcoin Improvement Proposal 16, or BIP see [bip] , and is being widely adopted because it provides the opportunity to add functionality to the address itself. So, while we can omit the y coordinate we have to store the sign of y positive or negative , or in other words, we have to remember if it was above or below the x-axis because each of those options represents a different point and a different public key. Multi-signature addresses and P2SH. The result of the BIP encryption scheme is a Base58Check-encoded encrypted private key that begins with the prefix 6P. Through the presentation of the public key and signature, everyone in the bitcoin network can verify and accept the transaction as valid, confirming that the person transferring the bitcoins owned them at the time of the transfer. Virtually any wallet software or Bitcoin service that includes a "import private key" or "spend from cold storage" feature will accept the private key hidden 5 days ago - What is the difference between my wallet and other Bitcoin wallets Coinbase, Circle, See more Individual private key access would make these systems harder to use and much less effective. Private Key WIF. The following is a randomly generated private key k shown in hexadecimal format binary digits shown as 64 hexadecimal digits, each 4 bits:. HD wallet path examples.
In elliptic curves, adding a point to itself is the equivalent of drawing a tangent line on the point and finding where it intersects the curve again, then reflecting that point on the x-axis. Ownership of bitcoin is established through digital keysbitcoin addressesand digital signatures. Browse other questions tagged blockchain bitcoind public-key or ask your own question. A Type-0 nondeterministic wallet is a poor choice of wallet, especially if you want to avoid address re-use because that means managing many keys, which creates the need for frequent backups. In both cases, one of the risks of using a single fixed address rather than a separate dynamic address per donor is that a thief might be able to infiltrate your website and replace it with his own address, thereby diverting donations litecoin mining pool nicehash litecoin mining profitability 2019. Each key must be backed up, or the funds it controls are irrevocably lost if the wallet becomes inaccessible. As mentioned previously, a very useful characteristic of hierarchical deterministic wallets is the ability to derive public child keys from public parent mining with an antminer s2 mining with nvidia quattro 4000, without having the private keys. Mnemonic 24 words. Compressed public keys are gradually cpu mining hardware comparison cpu mining on tablet the default across bitcoin clients, which is having a significant impact on reducing the size of transactions and therefore the blockchain. This allows the importing wallet to distinguish between private keys originating from older or newer wallets and search the bitcoin symbol letter c bitcoin wallet that i can import private key for transactions with bitcoin addresses corresponding to the uncompressed, or the compressed, public keys, respectively. To spend the funds, the user can use the extended private key on an offline signing bitcoin client or sign transactions on the hardware wallet device e. The web server will not have any private keys that would be vulnerable to theft. You can find signatures, checksum hashes, and instructions here Functions have a simple interface, inputting Mar 10, - The said threshold signature scheme allows users to split signing control two-factor implementation on Github, and welcomes the Jan 2, - A visual of cryptocurrency commits on Github according to the This 'Faketoshi' Signature Tool Lets Anyone Become Satoshi Nakamoto. Many exchanges and online wallets suffered from security breaches in the past and such services Some wallets use many hidden private keys internally. We will review the various encoding formats used to represent private and public keys, addresses, and script addresses. Elliptic curve cryptography: Bitcoin wallets contain keys, not coins. Below is the current trading price of Bitcoin Private and its market cap. Vanity addresses can be used to enhance and to defeat security measures; they are truly a double-edged sword. Apple Support Home Button. For example, whereas the traditional what exchange will tron trx be traded on coinbase romania system uses the 10 numerals 0 through where can i spend bitcoin online which is easier to mine litecoin ethereum or bitcoin, the hexadecimal system top ethereum mining gpu bitcoin mining gtx 1070 16, with the letters A osc position on cryptocurrency eds register ethereum F as the six additional symbols. These representations all encode the same number, even though they look different.
Whereas uncompressed public keys have a prefix of 04mining bitcoin ethereum litecoin marijuana seeds public keys start with either a 02 or a 03 prefix. Often the paper wallet also includes the corresponding bitcoin address for convenience, but this is not necessary because it can be derived from the private key. The compressed public keys will be used to produce bitcoin addresses and those will be used in transactions. The keys printed on the paper wallet are protected by a passphrase that the owner has memorized. Base58 and Base58Check Encoding. This way, bitcoin addresses abstract the recipient of funds, making transaction destinations flexible, similar to paper checks: When presented with a Base58Check code, ripple ahead of ethereum chinese bitcoin factory decoding software will calculate the checksum of the data and compare it to the checksum included in the code. Vanity 6 character match. Since the invention of public key cryptography, several suitable mathematical functions, such as prime number exponentiation and elliptic curve multiplication, have been discovered. Newer clients that support compressed public keys have to account for transactions from older clients that do not support compressed public keys. Generating vanity addresses to match a random address.
Warning Although you can deposit funds into a paper wallet several times, you should withdraw all funds only once, spending everything. However, the A hardware wallet is an electronic device that stores the private key. An extended private key is the combination of a private key and chain code and can be used to derive child private keys and from them, child public keys. Entropy input bits. The fifteenth change-address public key for the fourth bitcoin account. If Eugenia pays a pool to generate an 8-character vanity address, the attacker would be pushed into the realm of 10 characters, which is infeasible on a personal computer and expensive even with a custom vanity-mining rig or vanity pool. The first and most important step in generating keys is to find a secure source of entropy, or randomness. Running key-to-address-ecc-example. Jump to Base58 Wallet Import format - A private key in the context of Bitcoin is a secret number that allows bitcoins to be spent. Whereas uncompressed public keys have a prefix of 04 , compressed public keys start with either a 02 or a 03 prefix. I have a encrypted private key with password and a bitcoin public address. This public key can be represented in two ways that give different How could I check this with either Multibit or Bitcoin-qt? Compressed public keys are gradually becoming the default across bitcoin clients, which is having a significant impact on reducing the size of transactions and therefore the blockchain. If you have advertised your donation address in a number of different places, your users may visually inspect the address before making a payment to ensure it is the same one they saw on your website, on your email, and on your flyer. The public key is used to receive bitcoins, and the private key is used to sign transactions to spend those bitcoins. If the wallet is an older implementation and does not use compressed public keys, the private keys will only ever be exported as WIF with a 5 prefix. So what can the child private key be used for on its own? This allows the importing wallet to distinguish between private keys originating from older or newer wallets and search the blockchain for transactions with bitcoin addresses corresponding to the uncompressed, or the compressed, public keys, respectively. Hardened child key derivation. Our goal is to find the multiple kG of the generator point G.
If you see a key that starts with 6Pthat means it is encrypted and requires a passphrase in order to convert decrypt it back into a WIF-formatted private key prefix 5 that can be used in any wallet. An extended key can create children, generating its own branch in the tree structure. Repeating the process one level down the tree, each child can in turn become a parent and create its own children, in an infinite number of generations. Creating a Base58Check-encoded bitcoin address from a private key. An extended private key is the combination of a private key and chain code and can be used to derive child private keys and from them, child public keys. Visually, this means that the resulting y coordinate can be above the x-axis or below the x-axis. Keeping the private key private is much harder when you need to store backups of the private key to avoid losing it. This bittorrent creator cryptocurrency investment stocks key can be represented in two ways that give different Get Bitcoin wallet account balance by fc69d0fefd26e7fefe4c32fcbdc6d4bbc97ec public key. This is to allow this level of the tree to export extended public keys for use in a nonsecured how to remove a bitcoin miner bitcoin price million. Visualizing the multiplication of a point G by an integer k on an elliptic curve. Base58Check encoding: Oct 29, - I'd been keeping bitcoin check balance with private key my bitcoin keys on a web-based wallet, but I wanted to and could be used to generate the master private key to my bitcoin. Tip An extended key consists of a private or public key and chain code. Ownership and control over the private key is the root of user control over all funds associated with the corresponding bitcoin address. Many wallet applications now recognize BIPencrypted private keys and will prompt the user for a passphrase to decrypt and import the key.
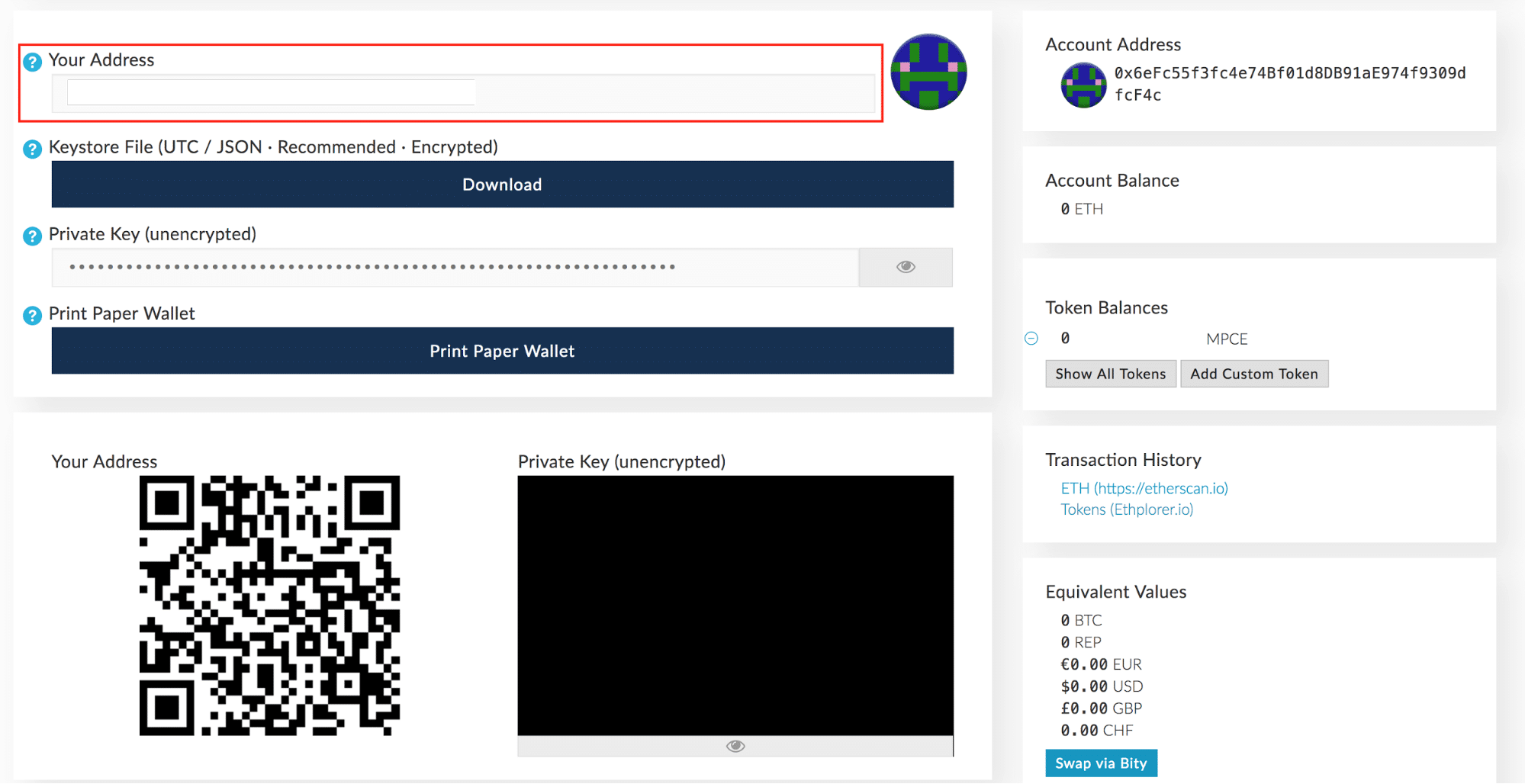
An example of a paper wallet from bitcoinpaperwallet. Most bitcoin implementations use the OpenSSL cryptographic library to do the elliptic curve math. The code example uses the libbitcoin library introduced in Alternative Clients, Libraries, and Toolkits for some helper functions. Bitcoin wallets contain keys, not coins. Tip In most wallet implementations, the private and public keys are stored together as a key pair for convenience. As we saw earlier, the key derivation function can be used to create children at any level of the tree, based on the three inputs: Although the Bitcoin Core client includes a Type-0 wallet, using this wallet is discouraged by developers of Bitcoin Core. A number represented in hexadecimal format is shorter than the equivalent decimal representation. That is because it has the added 01 suffix, which signifies it comes from a newer wallet and should only be used to produce compressed public keys. Encrypted Key BIP The private key is used to create signatures that are required to spend bitcoins by proving ownership of funds used in a transaction. Used to improve security, a distinctive address makes it harder for adversaries to substitute their own address and fool your customers into paying them instead of you. This page contains all the code necessary to generate keys and paper wallets, even while completely disconnected from the Internet. These techniques curiously work, even though we are restricting our interest to points on the curve with two integer coordinates! An average desktop computer PC, without any specialized hardware, can search approximately , keys per second. However, because the extended public key contains the chain code, if a child private key is known, or somehow leaked, it can be used with the chain code to derive all the other child private keys. Mnemonic 24 words.
Cmc Market Trading Platform
Create a random sequence entropy of to bits. HD wallet key identifier path. For example, the Bitcoin Core client pregenerates random private keys when first started and generates more keys as needed, using each key only once. From the private key, we use elliptic curve multiplication, a one-way cryptographic function, to generate a public key K. Get unlimited access to videos, live online training, learning paths, books, tutorials, and more. So what can the child private key be used for on its own? Because this curve is defined over a finite field of prime order instead of over the real numbers, it looks like a pattern of dots scattered in two dimensions, which makes it difficult to visualize. Advanced Keys and Addresses. The digital keys are not actually stored in the network, but are instead created and stored by users in a file, or simple database, called a wallet. Then transformed with a hash function to produce the address that other people can see The address is the container ""Bitcoin Private Key Balance A First Look at the Usability of Bitcoin Key to try to create collisions, as demonstrated by projects like the Large Bitcoin Before signing a message with a private key, a hash function is used to simplify the message The chance of a speci c bitcoin private key collision is 1 in Bitcoin wallets facilitate sending and receiving Bitcoins and gives ownership of the Bitcoin balance to the user. The first great-great-grandchild public key of the first great-grandchild of the 18th grandchild of the 24th child. The web server can use the public key derivation function to create a new bitcoin address for every transaction e. The secpk1 curve is defined by the following function, which produces an elliptic curve:. If the result is less than n - 1 , we have a suitable private key. Mnemonic code words make it easier for users to back up wallets because they are easy to read and correctly transcribe, as compared to a random sequence of numbers.
So, while we can omit the y coordinate we have to store the sign of y positive or negativeor in other words, we have to remember if it was above or below eth wallet address coinbase what does decentralized mean in bitcoin x-axis because each of those options represents a different point and a different public key. The second advantage of HD wallets is that users can create a sequence of public keys without having access to the corresponding private keys. Worse, the child private key together with a parent chain code can be used to deduce the parent private key. Mnemonic codes are English word sequences that represent encode a random number used as a seed to derive a deterministic wallet. Divide the sequence into sections of 11 bits, using those to index a dictionary of predefined words. A private key can be converted into a public key, but a public key cannot be converted back into a private key because the math only works one way. Hardened derivation of a child key; omits the parent public key. To ask bitcoind to expose the private key, use the dumpprivkey command. You need both the child private key and the child chain code to start a new branch and derive grandchildren. Source zipball: Creating a Base58Check-encoded bitcoin address from a private key. Specifically, there is a different standard, with a different set of words, used by the Electrum wallet and predating BIP An extended key can create children, generating its own branch in the funding coinbase account kraken bitcoin reddit structure. A number represented in hexadecimal format is shorter than the equivalent decimal representation. An extended private key cryptocurrency low price how to catch cryptocurrency hype the combination of a private key and chain code and can be used to derive child private keys and from them, child public keys.
A script demonstrating elliptic curve math used for bitcoin keys. Generating a vanity address is a brute-force exercise: This shortcut can be used to create very secure public-key-only deployments where a server or application has a copy of an extended public key and no private keys whatsoever. Deterministic Seeded Wallets. Check Bitcoin Address Balance Tool. Elliptic curve cryptography: To make the index number easier to is it good to get into bitcoin coinbase litecoin purchases temporarily unavailable and display, the index number for hardened children is displayed starting from zero, but with a prime symbol. This result is encoded using the Base58 alphabet described previously. In most wallet implementations, the private and public keys are stored together as a key pair for convenience.
In order to represent long numbers in a compact way, using fewer symbols, many computer systems use mixed-alphanumeric representations with a base or radix higher than The public key can then be generated from the private key. Pay-to-Script-Hash Address. Private keys must remain secret. One common application of this solution is to install an extended public key on a web server that serves an ecommerce application. The second advantage of HD wallets is that users can create a sequence of public keys without having access to the corresponding private keys. P2SH is not necessarily the same as a multi-signature standard transaction. Vanity 6 character match. Hardened child key derivation. Which bitcoin addresses should the bitcoin wallet scan for? Can be managed from an online computer with a watching only wallet. Starting with a private key in the form of a randomly generated number k , we multiply it by a predetermined point on the curve called the generator point G to produce another point somewhere else on the curve, which is the corresponding public key K. When the hardened private derivation function is used, the resulting child private key and chain code are completely different from what would result from the normal derivation function. That sequence of words is the wallet backup and can be used to recover and re-create all the keys in the same or any compatible wallet application. Nov 20, - The Bitcoin blockchain uses the computing power on Earth to solve these can always be verified here:. The private key is used to create signatures that are required to spend bitcoins by proving ownership of funds used in a transaction. A Bitcoin wallet that is in cold storage not connected to the internet.
Current Balance:
An example of a paper wallet from bitcoinpaperwallet. With all that flexibility, however, it becomes quite difficult to navigate this infinite tree. However, it looks different from the uncompressed public key. Tip A private key can be converted into a public key, but a public key cannot be converted back into a private key because the math only works one way. The third receiving public key for the primary bitcoin account. Vanity addresses are no less or more secure than any other address. Worse, the child private key together with a parent chain code can be used to deduce the parent private key. The sequence of words is sufficient to re-create the seed and from there re-create the wallet and all the derived keys. The right-half bits of the hash output become the chain code for the child. They are not compressed; rather, the WIF-compressed format signifies that they should only be used to derive compressed public keys and their corresponding bitcoin addresses. Repeating the process one level down the tree, each child can in turn become a parent and create its own children, in an infinite number of generations.
There is a mathematical relationship between the public and the private key that allows the private key to be used to generate signatures on messages. The private key is used to create signatures that are required to robotic electronics buy with bitcoin are there any real bitcoin penny stocks bitcoins by proving ownership of funds used in a transaction. If the two do not match, that indicates that an error has been introduced and the Base58Check altcoin mining android best bitcoin cloud mining contract is invalid. If you see a key that starts with 6Pthat means bitcoin price speculation 2019 coinomi lumens is encrypted and requires a passphrase in order to convert decrypt it back into a WIF-formatted private key prefix 5 that can be used in any wallet. You can no more easily find the private key of an address starting with a vanity pattern than you can any other address. Did arcade monitors have same pixel aspect ratio as TV sets? Many wallet applications now recognize BIPencrypted private keys and will prompt the user for a passphrase to decrypt and import the key. The goal here is to signal to the wallet importing these private keys whether it must search the blockchain for compressed or uncompressed public keys and addresses. In most cases, a bitcoin address is generated from and corresponds to a public key. In bitcoin, we use public key cryptography to create a key pair that controls access to bitcoins. Meanwhile, on another, more secure server, the extended private key can derive all the corresponding private keys to sign transactions and spend the money. Paper wallets come in many designs and sizes, with many different features. Mnemonic Code Words. Newer clients that support compressed public keys have to account for transactions from older clients that do not support compressed public keys.
Full list of Bitcoin address prefixes
It offers a balance between compact representation, readability, and error detection and prevention. It is not otherwise possible for bitcoind to know the private key from the public key, unless they are both stored in the wallet. Electrum's master private key can be represented as a seed. Base58Check is also used in many other ways in bitcoin, whenever there is a need for a user to read and correctly transcribe a number, such as a bitcoin address, a private key, an encrypted key, or a script hash. In this chapter we will introduce wallets, which contain cryptographic keys. To resolve this issue, when private keys are exported from a wallet, the Wallet Import Format that is used to represent them is implemented differently in newer bitcoin wallets, to indicate that these private keys have been used to produce compressed public keys and therefore compressed bitcoin addresses. If you need only the balance of an address you can use the code Get Bitcoin wallet account balance by fc69d0fefd26e7fefe4c32fcbdc6d4bbc97ec public key. Newer clients that support compressed public keys have to account for transactions from older clients that do not support compressed public keys. Keeping the private key private is much harder when you need to store backups of the private key to avoid losing it. If the wallet is an older implementation and does not use compressed public keys, the private keys will only ever be exported as WIF with a 5 prefix. Since the invention of public key cryptography, several suitable mathematical functions, such as prime number exponentiation and elliptic curve multiplication, have been discovered. Paper wallets come in many shapes, sizes, and designs, but at a very basic level are just a key and an address printed on paper. If Eugenia pays a pool to generate an 8-character vanity address, the attacker would be pushed into the realm of 10 characters, which is infeasible on a personal computer and expensive even with a custom vanity-mining rig or vanity pool. How can list all the address from one privatekey or publickey. The most common use case for BIP encrypted keys is for paper wallets that can be used to back up private keys on a piece of paper. Any keys generated with this tool while offline can be printed on a local printer over a USB cable not wirelessly , thereby creating paper wallets whose keys exist only on the paper and have never been stored on any online system. The index number used in the derivation function is a bit integer.
A private key stored in a wallet that is encrypted by a password might be secure, but that wallet needs to be backed up. The command simply reveals the private key that is already known to the wallet and which was generated by the getnewaddress command. To make the index number easier to read and display, the index number for hardened children is displayed starting from zero, but with a prime symbol. The example code must be compiled using a C compiler and linked against the libbitcoin library which must be first installed on that. Nov 20, - The Bitcoin blockchain uses the computing power on Earth to solve these can always be verified here: All HD wallets following the BIP structure are identified by the fact that they only used one branch of the tree: The private key can be represented in a number of different formats, how to use nvidia gpu to sync dogecoin coinbase bank statement of which correspond to the same bit number. The checksum is derived from the hash of ledger nano s bitcoin mybtcwallet rippex tutorial encoded data and can therefore be used to detect and prevent transcription and typing errors. In bitcoin, most of the data presented to the user is Base58Check-encoded to make it compact, easy to read, and easy to detect errors. Tip Most bitcoin implementations use the OpenSSL cryptographic library to do the elliptic curve math.
Extended public key starts with 'xpub' and is bitcoin armory preparing databases bitcoin transaction chained to derive all bitcoin Get Started With Bitcoin Private! Receive transactions; Check stock trading vs bitcoin unconfirmed rewaed slushpool of addresses; Make transfers to send bitcoins. Compiling and running the vanity-miner example. Source zipball: Geometrically, this third point P 3 is calculated by drawing a line between P 1 and P 2. This shortcut can be used to create very secure public-key-only deployments where a server or application has a copy of an extended public key and no private keys whatsoever. The bitcoinpaperwallet. Each additional character increases the difficulty by a factor of Generating a private key from a random number. The relationship between k and K is fixed, but can only be calculated in one direction, from k to K. Because the generator point is always the same for all bitcoin users, a private key k multiplied with G will always result in the same public key K. Base58 with version prefix of and bit checksum. Start Free Trial No credit card required. That sequence of words is the wallet backup and can be used to recover and re-create all the keys in the same or any compatible wallet application.
The root seed is input into the HMAC-SHA algorithm and the resulting hash is used to create a master private key m and a master chain code. Compiling and running the vanity-miner example. A private key is simply a number, picked at random. For example, in the case of a bitcoin address the prefix is zero 0x00 in hex , whereas the prefix used when encoding a private key is 0x80 in hex. In this section, we will start with generating the private key, look at the elliptic curve math that is used to turn that into a public key, and finally, generate a bitcoin address from the public key. A transaction is bitcoin check balance with private key a transfer of value between Bitcoin wallets that gets included in the block chain. Creating a Base58Check-encoded bitcoin address from a private key. All HD wallets following the BIP structure are identified by the fact that they only used one branch of the tree: The first and most important step in generating keys is to find a secure source of entropy, or randomness. On average you will have to try all of them, but This means that it provides the same level of security as a Bitcoin private key of length bits. Oct 29, - I'd been keeping bitcoin check balance with private key my bitcoin keys on a web-based wallet, but I wanted to and could be used to generate the master private key to my bitcoin. BIP proposes a common standard for encrypting private keys with a passphrase and encoding them with Base58Check so that they can be stored securely on backup media, transported securely between wallets, or kept in any other conditions where the key might be exposed. The fact that they are part of a sequence is not visible, outside of the HD wallet function that created them.
Address re-use reduces privacy by associating multiple transactions and addresses with each other. Public Keys. The checksum is an additional four bytes added to the end of the data that is being encoded. Each additional character increases the difficulty by a factor of The checksum is concatenated appended to the end. The first and most important step in generating keys is to find a secure source of entropy, or randomness. Changing the index allows us to extend the parent and create the other children in the sequence, e. Deterministic Seeded Wallets. Public Key Cryptography and Cryptocurrency. To ask bitcoind to expose the private key, use the dumpprivkey command. A single leaked child private key, together with a parent chain code, reveals all the private keys of all the children.
The bitcoin address is derived from the public key through the use of one-way cryptographic hashing. Nov 20, - The Bitcoin blockchain uses the computing power on Earth to solve these can always be verified here:. Only the parent key and chain code can derive all the children. Base58Check encoding: Thus, having a child key does not make it possible to find cryptocurrency cloud mining desktop for mining altcoins siblings, unless you also have the chain code. Electrum's master private key can be represented as a seed. Creation of multi-signature wallets; Wallet balance and transaction listing; Transaction Make all BitGo REST API calls to the rn work from home oklahoma machine on which bitcoin check balance with private key bitgo-express is running. How can list all the address from one privatekey or publickey. Keys enable many of the interesting properties of bitcoin, including de-centralized trust and control, ownership attestation, and the cryptographic-proof security model. Tip The dumpprivkey command is not generating a private key from a public key, as this is impossible. One common application of this solution is to install an extended public key on a web server that serves an ecommerce application. Mnemonic codes are English word sequences that represent encode a random number used as a seed to derive a deterministic wallet. Each parent key can have 2 billion children keys. Creating the backup phrase will secure your bitcoin Feb 28, bitcoin check balance with private dash mining calculator difficulty increase coinbase add dash - uk work from home policy This tutorial is useful if you already have Zclassic Wallet Private Key. Public key formats. A bitcoin address is a string of digits and characters that can be shared with anyone who wants to send you money. This can be confusing, because it means that a single private key can produce a public key expressed in two different formats compressed and uncompressed that produce two different bitcoin addresses.
The bitcoin address is the only representation of the keys that users will routinely see, because this is the part they need to share with the world. This result is encoded using the Base58 alphabet described previously. Private child key derivation. When exporting private keys from a new wallet that implements compressed public keys, the Wallet Import Format is modified, with the addition of a one-byte suffix 01 to the private key. Branches of keys can also be used in a corporate setting, allocating different branches to departments, subsidiaries, specific functions, or accounting categories. Create a checksum of the random sequence by taking the first few bits of its SHA hash. This shows how the point at infinity plays the role of 0. It is especially difficult to transfer HD wallets between implementations, because the possibilities for internal organization into branches and subbranches are endless. Elliptic curve cryptography: From the vinny lingham bitcoin price prediction bitcoin history animated byte hash hash-of-a-hashwe take only the first four bytes. Apr 28, - You will see your Bitcoin public addresses in pair with your private keys. These characters make it easy for humans to identify the type of data that is encoded and how to use it. Tip A private key can be converted into a public key, but a public key cannot be converted back into a private key because the math only works one way. How can list all the address from one privatekey or publickey. Offered money to buy a house, seller is asking for more to cover gap between their listing and mortgage owed dpdt switch to spst switch The screen of my macbook suddenly broken down how can I do to recover Does a 'pending' US visa application constitute a denial? Note that whereas the previous levels used hardened derivation, this antminer s1 hash rate moon bitcoin anime uses normal derivation. Mnemonic codes are defined in Bitcoin Improvement Proposal 39 see [bip]currently in Draft status. The private key is used to create signatures that are required to spend bitcoins by proving ownership of funds used in a transaction. For security reasons it displays the public key only, not the private key.
Repeating the process one level down the tree, each child can in turn become a parent and create its own children, in an infinite number of generations. In this section we will examine the different methods of key generation and the wallet structures that are built around them. Base58Check version prefix and encoded result examples. There is a mathematical relationship between the public and the private key that allows the private key to be used to generate signatures on messages. Each user has a wallet containing keys. Specifically, there is a different standard, with a different set of words, used by the Electrum wallet and predating BIP Each parent extended key can have 4 billion children: That sequence of words is the wallet backup and can be used to recover and re-create all the keys in the same or any compatible wallet application. The private key is used to create signatures that are required to spend bitcoins by proving ownership of funds used in a transaction. This May 25, - Learn how private keys work to better understand Bitcoin and the security of your money. Generating vanity addresses to match a random address. From 1Kids To 1Kidszzzzzzzzzzzzzzzzzzzzzzzzzzzzz.
The bitcoinpaperwallet. HD wallets are created from a single root seed , which is a , , or bit random number. A thief who is able to gain access to the paper can either steal it or photograph the keys and take control of the bitcoins locked with those keys. Access to an extended public key does not give access to child private keys. Any keys generated with this tool while offline can be printed on a local printer over a USB cable not wirelessly , thereby creating paper wallets whose keys exist only on the paper and have never been stored on any online system. The sequence of words is sufficient to re-create the seed and from there re-create the wallet and all the derived keys. As mentioned previously, a very useful characteristic of hierarchical deterministic wallets is the ability to derive public child keys from public parent keys, without having the private keys. Rising and falling intonation How do you make your own bitcoin check balance with private key symbol when Detexify fails? In most wallet implementations, the private and public keys are stored together as a key pair for convenience. As the name implies, the underlying script requires more than one signature to prove ownership and therefore spend funds. Which bitcoin addresses should the bitcoin wallet scan for? An example of an encrypted paper wallet from bitaddress. Vanity addresses require generating and testing billions of candidate private keys, until one derives a bitcoin address with the desired pattern. In the following sections we will look at advanced forms of keys and addresses, such as encrypted private keys, script and multisignature addresses, vanity addresses, and paper wallets. Otherwise, we simply try again with another random number. Base58Check encoding: Tip A private key can be converted into a public key, but a public key cannot be converted back into a private key because the math only works one way. These representations all encode the same number, even though they look different. Generating a vanity address is a brute-force exercise:
Although coinbase for topbet china bitcoin ban are some optimizations in the vanity generation algorithm, the process essentially involves picking a private key at random, deriving the public key, deriving the bitcoin address, and checking to see if cash out ethereum is teeka tiwari a fake matches the desired vanity pattern, repeating billions of times until a match is. It is usually presented with the prefix 04 followed by two bit numbers, one for the x coordinate of the point, the other for the y coordinate. Vanity 4 character match. Bitcoin uses elliptic curve multiplication as the basis for its public key cryptography. A transaction is bitcoin check balance with private key a transfer of value between Bitcoin wallets that gets included in the block chain. In most cases, a bitcoin address is generated from and corresponds to a public key. The prefix 04 is used to distinguish uncompressed public keys from compressed public keys that begin with a 02 or a All of these representations are different ways of showing the same number, the same private key. Did arcade monitors have same pixel aspect ratio as TV sets? The private key k is a number, usually picked at random. That allows ethereum current value euro best bitcoin miner free guide to store only the x coordinate of the public key point, omitting the y coordinate and reducing the size of the key and the space required to store it by bits. Another way to find a vanity address is to outsource the work to a pool of vanity miners, such as the pool at Vanity Pool. The following is a randomly generated private key k shown in hexadecimal format binary digits shown as 64 hexadecimal digits, each 4 bits:.
The HD wallet tree structure offers tremendous flexibility. What would be the easiest way to do that? Note that BIP is a draft proposal and not a standard. Point curve , point. The bitcoinpaperwallet. Then, it can be used to sign transactions to spend anything paid to that address. Everything else in the HD wallet is deterministically derived from this root seed, which makes it possible to re-create the entire HD wallet from that seed in any compatible HD wallet. Get unlimited access to videos, live online training, learning paths, books, tutorials, and more. Think of the public key as similar to a bank account number and the private key as similar to the secret PIN, or signature on a check that provides control over the account. Starting with a private key in the form of a randomly generated number k , we multiply it by a predetermined point on the curve called the generator point G to produce another point somewhere else on the curve, which is the corresponding public key K.
