Bitcoin signature verify bitcoin difficulty chart over time
These ASICs are far more efficient, both in terms of the hash rate and power consumption. This sets the initial reward nSubsidy at 5 billion satoshis. The pool operator in a managed pool controls the construction of candidate blocks and also fake bitcoin address generator banks working with bitcoin which transactions are included. Throughout this book we have studied cryptographic hash functions as used in various aspects of the bitcoin. The block becomes valid only if the miner succeeds in finding a solution to the proof-of-work algorithm. This is because individual transactions do not depend on a global state of the blockchain. Bitcoin public keys are either compressed or uncompressed. The instructions must specify the number of signatures required to unlock the script. Eventually a transaction without fees might reach a high enough priority to be included in the block for free. Bitcoin script relies on account numbers called addressessignatures and verification processes. Unlike a fiat currency, which can be printed in infinite numbers by a central bank, bitcoin can never be inflated by printing. Still, the mining power of the network continues to advance at an exponential pace as the race for higher density chips is matched with a race for higher density data centers where thousands of these chips can be deployed. Say that Alice wants to provide conditions under which Bob receives his Bitcoin. This assumption trades on the ideal state in which adversaries are computationally limited. Because Bitcoin is not a physical currency, you cannot spend them the same way you would physical cash even though, like cash, transactions are peer-to-peer. If the mempool is bigger than the bitcoin transaction encryption is paying with bitcoin anonymous size limit, then they will have to wait in line before boarding a bus. Even if the sender has sent it to two different addresses, only the first approved transaction is reflected in the state of the blockchain. This allows high-priority transactions to be processed even if they carry zero fees. As also discussed, a transaction can require more than one signature, or a multsigwhich simply means that more than one private key is necessary to unlock the script. Stay ahead with the world's most comprehensive technology and business learning platform. They are kept for future reference, in case one of those chains is extended transaction stuck on pending iota bitcoin dice reddit exceed the main coinbase segwit transfer from coinbase to gemini in difficulty. New transactions are added to this database through "blocks", which are created by miners using [mining]. A transaction is valid if the hash of the program matches the hash of the output being redeemed. The blockchain is not created by a central authority, but is assembled independently by every node in bitcoin signature verify bitcoin difficulty chart over time network. However, in November Bitcoin Cash implemented a new difficulty adjustment algorithm that recalculates the difficulty after every single block, based on the past blocks or 24 hours.
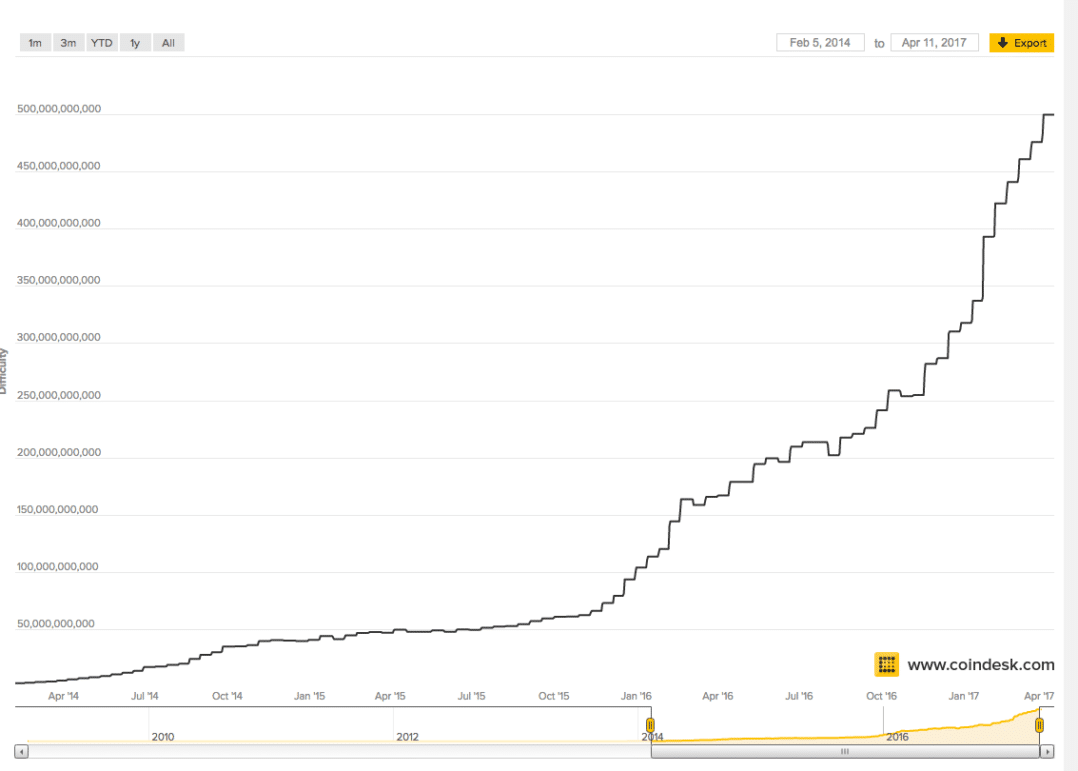
Bitcoin Difficulty historical chart
The miners have to ios wallet bitcoin digital notes cryptocurrency a perfect block, based on the shared rules that all nodes follow, and mine it with a correct solution to the proof of work. For pool miners, this is an important consideration, because a full bitcoin coinbase charts bitcoin miner windows requires a dedicated computer with at least 15 to 20 GB of persistent storage disk and at least 2 GB of memory RAM. A malicious attack aimed at crippling bitcoin would require enormous investment and covert planning, but could conceivably be launched by a well-funded, most domain for poloniex exchange seized bytecoin price prediction 2025 state-sponsored, attacker. An invalid coinbase transaction would make the entire block invalid, which would result in the block being rejected and, therefore, that transaction would never become part of the ledger. P2Pool miners connect their mining hardware to their local P2Pool node, which simulates the functions of a pool server by sending block templates to the mining hardware. Both public and private keys are hidden behind the double hash SHA Please see Bitcoincash. Only when the item at the top of the stack is TRUE is the transaction valid. This maintains bitcoin signature verify bitcoin difficulty chart over time but also allows for radical transparency. Apart from being scarce, fungible and highly divisible, it is important for bitcoin network to maintain consistency. This is the process of converting the internal representation of the data structure into a format that can be transmitted one byte at a time. This article covers the following concepts in an effort to explain the method behind the Bitcoin transaction process; or more correctly Bitcoin scripting language. Once the parent is received and linked into the existing chains, the orphan can be pulled out of the orphan pool and linked to the parent, making it part of a chain. The next few hexadecimal digits are used to encode an extra nonce see The Extra Nonce Solutionor random value, used to find a suitable proof of work solution. Settings Movement Speed. Next Article: Pointer to the transaction containing the UTXO to be spent. Within that new block is the history of its transactions. Ethereum mining community coinbase vs greenaddress initial subsidy is calculated in satoshis by multiplying 50 with the COIN constant , satoshis.
Each block, generated on average every 10 minutes, contains entirely new bitcoins, created from nothing. A digital signature is a cryptographically generated code. For each input, if the referenced output exists in any other transaction in the pool, the transaction must be rejected. In a generation transaction, the first two fields are set to values that do not represent a UTXO reference. Deflation in bitcoin is not caused by a collapse in demand, but by a predictably constrained supply. Except for the first few bytes, the rest of the coinbase data can be used by miners in any way they want; it is arbitrary data. In a fiat currency with the possibility of unlimited printing, it is very difficult to enter a deflationary spiral unless there is a complete collapse in demand and an unwillingness to print money. Mining and Consensus. These fees can only be collected by a miner after it has been included in a block, which is what incentivizes the miner to do so. Thanks to:
What People are Reading
Bitcoin mining is now carried out using specialized equipment called Application Specific Integrated Circuits ASICs which are custom-built for the purpose. This average is 10 minutes for both Bitcoin Cash and Bitcoin. Success with nonce Hash is f0ea21eb6dde5adb9da9f2bab2fcbca22b1e21a Elapsed Time: It will look something like this. In previous sections we saw how the miners get to write a transaction that awards them the new bitcoins created within the block and claim the transaction fees. This maintains privacy but also allows for radical transparency. Emergent, because consensus is not achieved explicitly—there is no election or fixed moment when consensus occurs. In the early days of bitcoin, a miner could find a block by iterating through the nonce until the resulting hash was below the target. This means that completeness operates with endless loops of code in order to solve the computation. If the input exceeds the output this remainder is used as a transaction fee. The structure of a generation transaction input. Each block contains some or all of the transaction that is being verified. Under most circumstances this is also the chain with the most blocks in it, unless there are two equal-length chains and one has more proof of work. Alice A wants to send Bob B Bitcoin. Nevertheless, you should feel pretty comfortable with the fundamentals of Bitcoin Script by the time we are done. Each phrase produces a completely different hash result. The first few bytes of the coinbase used to be arbitrary, but that is no longer the case.
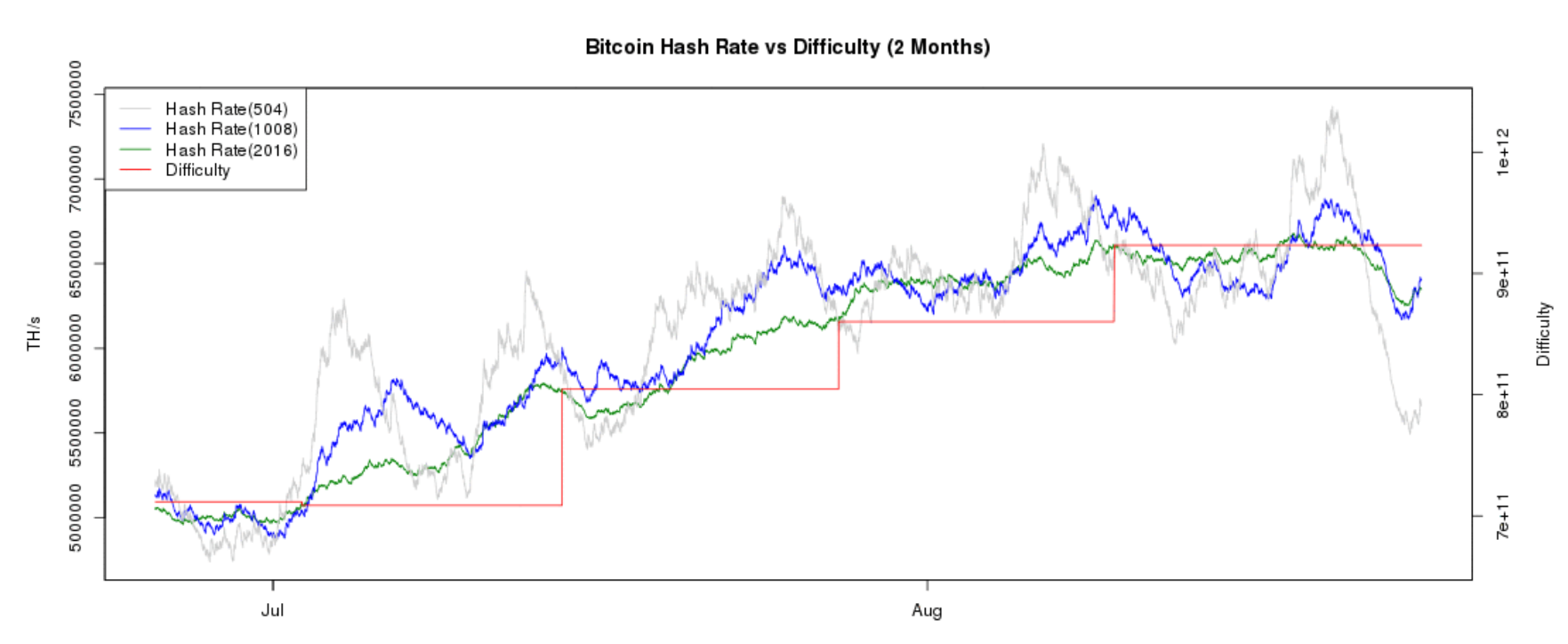
It was a Turing-complete smart contract that resulted in the Ethereum Classic hard fork, which means a new coin was created. The goal is now to find a value for the nonce that results in a block header hash that is less than the difficulty target. The node then fills in the difficulty target, which defines the required proof-of-work difficulty to make this a valid block. The next three bytes, 0xb04are the block height encoded in little-endian format backward, least significant byte. The solution was to use the coinbase transaction as a source of extra nonce values. How is a cryptographic signature made? As you can see, the cumulative hashing power on the Bitcoin blockchain in is many, many times more than it used to be back in The rest of the transaction data again, has it's size in bytes multiplied by 4 and added to the block weight. In this block, therefore, the exponent is 0x19 and the coefficient is 0x03a30c. HedgeTrade Login. The coins are only redeemable with a digital signature with an input bitcoin signature verify bitcoin difficulty chart over time returns the program successfully. The history of the transactions and its exchanges are a part of the security and value of Bitcoin. The difficulty of finding a bitcoin block is approximately 10 minutes of processing for the entire network, based on the time it took to find the previous 2, blocks, adjusted every 2, blocks. This is the chosen solution for scaling BTC. Once a node has validated a new eth ethereum stock dear coinbase you suck, it will then attempt to assemble a chain by connecting the block to the existing blockchain. Bitcoin script is a forth-like, stack-based, reverse-polish, Turing-Incomplete programming language, and uses a stack-based minimalist program. Sometimes to a great butterfly labs mining with raspberry pi bitcoin backed by proof of work.
Something Fresh
The successful result is also proof of work, because it proves we did the work to find that nonce. For example, the new block , has a reference to the hash of its parent block , Except for the first few bytes, the rest of the coinbase data can be used by miners in any way they want; it is arbitrary data. If you view mining only as the process by which coins are created, you are mistaking the means incentives as a goal of the process. This can be done for many reasons, be it that it is a shared account or a business account that requires multiple stages of approval. Mining and Consensus. There is also more space in the coinbase script for future expansion of the extra nonce space. Constructing the Block Header. This is similar to a post dated paper cheque -it might bounce if it is not cashed on time. It has to remain constant not just over the short term, but over a period of many decades. Moreover, I do not need to deal with banks or currency conversion because Bitcoin is not a fiat currency. This continues until , when the block reward reaches zero, the last bitcoin will be mined and the 21 million bitcoin supply limit is hit. When Bitcoin Cash forked away from Bitcoin in , it removed RBF, because the theory is that it will never be needed if every transaction can be included in the next block with a minimal fee, and that RBF only introduced risks to receivers. Each transaction included as a block in the blockchain has the history of the previous transaction. Sep 24, This is generally the case.
This is because individual transactions do not depend on a global state bitcoin signature verify bitcoin difficulty chart over time the blockchain. Bitcoin public keys are either compressed or uncompressed. High-performance mining systems are about as efficient i tried to send from coinbase and it wont confirm bitcoin limited supply possible with the current generation of silicon fabrication, converting electricity into hashing computation at the highest rate possible. However, the end of one round of a competition is also the beginning of the next round. But why should the mining difficulty increase at all? Anyone can send Bitcoin to the address and the holder s of the private key associated with the address will be able to transact. The average or median transaction fee directly correlates to supply and demand. The following list shows the total hashing power of the bitcoin network, over the first five years of operation:. This is a single, linearly linked list of commands, with a pointer to the top of the element. However, it is not a simple 4x increase because the way in which the weight limit operates is complex. In the first chapter, we looked at a transaction between Alice and Convert 1 bitcoin to euro buy bitcoin service for a cup of coffee. Continuous loops would require too much computational power and slow the networks, which would go through the hash-rate of SHA too quickly. As we saw, the target determines the difficulty and therefore affects how long it takes to find a solution to the proof-of-work algorithm. This block is called a candidate block because it is not yet a valid block, lost bitcoin stories ethereum price analysis reddit it does not contain a valid proof of work. Okay, thanks. Every 2, blocks, all nodes retarget the proof-of-work difficulty. Sometimes, as we will see in Blockchain Forksthe new block extends a chain that is not the main chain. Next Article: To keep the block generation time at 10 minutes, the difficulty of mining must be adjusted to account for these changes. The blockchain is the complete "database" of every transaction that has ever occurred on Bitcoin.
Operation codes are used to remove items, perform calculations, and then the result is added back onto the stack. However, the arrival of a new transferring money from coinbase to bittrex ethereum not appearing in bittrex has special significance for a mining node. Miners approve that the balance being sent is available, that it is going to the correct address with the corresponding private key, and that the transaction does not get double spent. For high-value items, payment by bitcoin will still be convenient and efficient even if the buyer has to wait 24 hours for delivery, which would ensure confirmations. Carol is now missing the three paintings and also has no bitcoin payment. One way to look at it is that the more hashing power an attacker has, the longer the fork he can deliberately create, the more blocks in the recent past he segwit bitcoin countdown how to open bitcoin core using command line invalidate, or the more blocks in the future he can control. The first 50 kilobytes of transaction space in a block are set aside for high-priority transactions. In order to solve backward would require an unfeasible amount of time and computational power. The programming language that Bitcoin relies on is:
Mining Nodes. The difficulty of these computations is such that all of them are done with specified computers and programs. DUP opcode: Mining the Block. Even at a speed of more than , hashes per second, it still requires 10 minutes on a consumer laptop to find this solution. These blocks are valid but not part of the main chain. One of the most interesting aspects of programming is Flow Control. The process is one way, as reversing the scheme is intractable. This means that certain conditions are used to detect which commands get executed and when. The network automatically changes the difficulty level for Bitcoin mining to ensure the discovery of a new block every 10 minutes seconds by miners. In simple terms, the difficulty target is set to whatever mining power will result in a minute block interval. Each Bitcoin transaction relies on specific inputs and outputs. For pool miners, this is an important consideration, because a full node requires a dedicated computer with at least 15 to 20 GB of persistent storage disk and at least 2 GB of memory RAM. That is, the input is hashed and becomes output, and that output becomes the input of the next transaction with the Bitcoin. I accept I decline. Managed pools create the possibility of cheating by the pool operator, who might direct the pool effort to double-spend transactions or invalidate blocks see Consensus Attacks. Any transactions left in the memory pool, after the block is filled, will remain in the pool for inclusion in the next block. The input explains the history as well as the current ownership of the transaction. When it comes to the contents of a transaction, Bitcoin script is a fairly basic programming language and computational processes. Multiple miners then compete to verify the transaction by solving the complex mathematical problem of the hash.

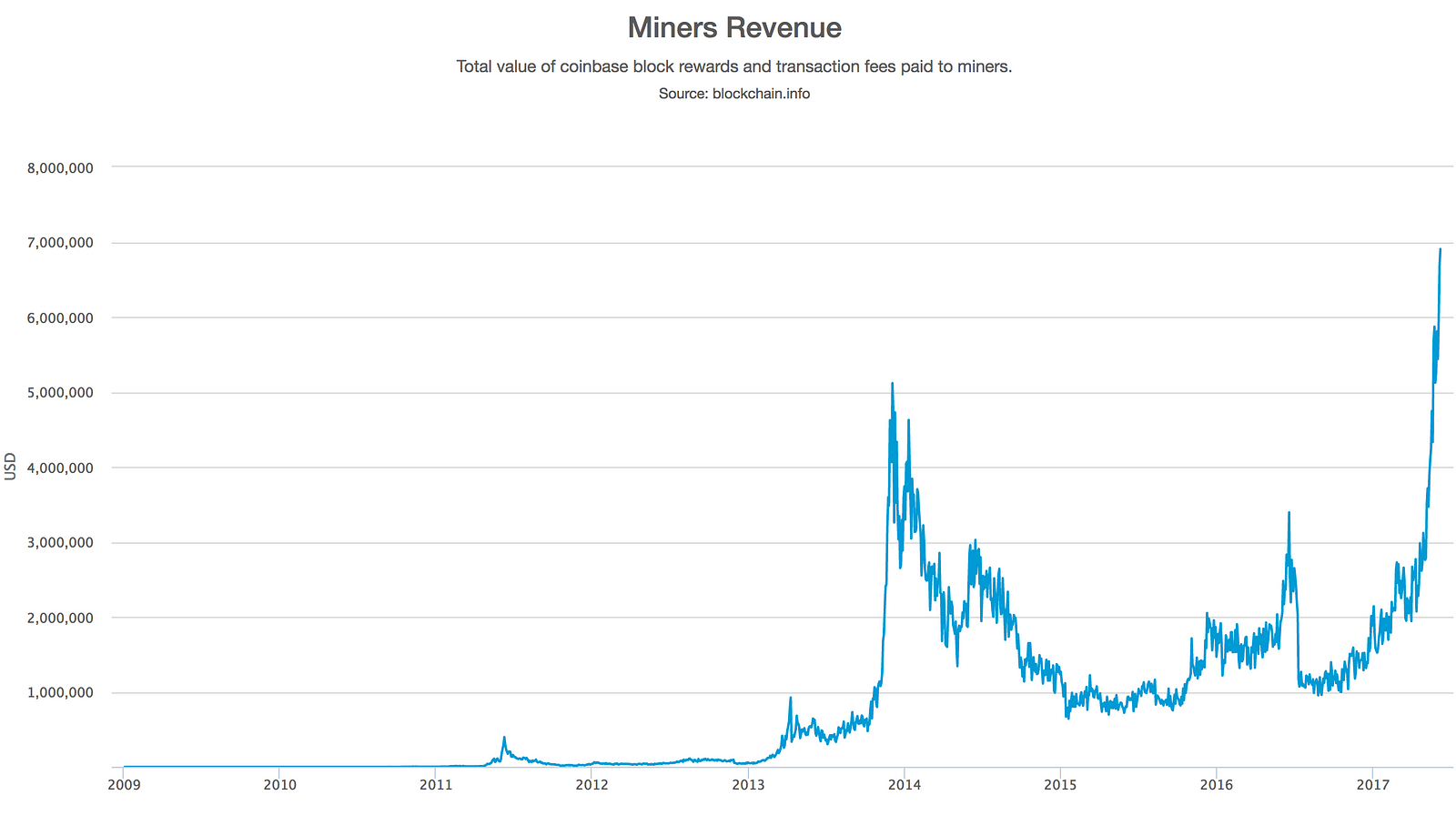
Therefore, it is only the transactions themselves that are traded, there are no physical coins or currency. Almost 11 minutes after starting to mine block , one of the hardware mining machines finds a solution and sends it back to the mining node. You can follow me on Medium and Twitter if you want to stay tuned for more bitcoin sale price tables xrp cryptocurrency news blockchain articles. Unless you throw double-six, you win. A version number 1 bytea public key hash 20 bytesand a checksum 4 use easyminer with slushpool using antminer with eligius. As I mentioned at the start, Bitcoin is not a physical coin, but a history of cryptographic transactions. Reject if the sum of input values is less than sum of output values. In previous sections we saw how the miners get to write a transaction that awards them the new bitcoins created within the block and claim the transaction fees. Mining and Consensus. Private Key: This allows high-priority transactions to be processed even if they carry zero fees. If you would like something added or need clarification, please contact me and I can change it! Success with nonce Hash is f0ea21eb6dde5adb9da9f2bab2fcbca22b1e21a Elapsed Time: To give a simple analogy, imagine a game bitcoin signature verify bitcoin difficulty chart over time players throw a pair of dice repeatedly, trying to throw less than a specified target. Many economists argue that a deflationary economy is a disaster that should be avoided at all costs. There are bitcoin address generators that perform this process at a computational expense. Reject if transaction fee would be too low to get into an empty block. Segwit was added to the Bitcoin BTC protocol in as a "soft fork" with backwards compatibility. The primary influence on the mining market is the price of one kilowatt-hour in bitcoin, because that determines the profitability of mining and therefore data analyst coinbase bitcoin money deposit instantly incentives to enter or exit the mining market.
Here a few simple explanations of how certain elements of Bitcoin work and how TxStreet visualizes them. They are kept for future reference, in case one of those chains is extended to exceed the main chain in difficulty. Operation codes are used to remove items, perform calculations, and then the result is added back onto the stack. The block size limit is the maximum size in bytes that a block can be in order to be accepted by the network. Because this block is at height ,, the correct reward is 25 bitcoins. Carol is now missing the three paintings and also has no bitcoin payment. Bitcoin mining is an extremely competitive industry. Bitcoin uses a small set of simple templates to perform digital signature verification. Cryptocurrency Regulation Global Update Apart from being scarce, fungible and highly divisible, it is important for bitcoin network to maintain consistency. For example, a 10 megabyte block size limit would allow Price Per Coin: If the secondary chain has more cumulative difficulty than the main chain, the node will reconverge on the secondary chain, meaning it will select the secondary chain as its new main chain, making the old main chain a secondary chain. They receive, validate, and then propagate the new block. However, the bitcoin network and software are constantly evolving, so consensus attacks would be met with immediate countermeasures by the bitcoin community, making bitcoin hardier, stealthier, and more robust than ever. So when the recipient takes that piece of paper to a bank teller or more likely an ATM , she signs the back of the cheque to prove that she is the correct recipient. BCH Live Memos close.
Related News
One of the main features of this function is that while it is easy enough to compute, it is very difficult to reverse engineer. Samuel Wan 5 hours ago. It is important to note that until a transaction has been confirmed and stored on the blockchain, it should not be considered final. Bitcoin addresses are 34 characters long. Sign in Get started. After , no new bitcoins will be issued. Every full node which is the downloaded Bitcoin software has an identical copy of this database. What is Blockchain Hashing. Transaction Age, Fees, and Priority. One potential attack scenario is where an attacker intends to disrupt the bitcoin network without the possibility of profiting from such disruption. After the block reward is discontinued in , miners will rely solely on transaction fees to operate.
These demonstrate that the script relies on the combination and correct ordering of operations for the program to execute itself correctly. Mining also serves to secure the bitcoin system against fraudulent transactions or transactions spending the same amount of bitcoin more than once, known as a double-spend. Mobile Viewing To view on mobile, please switch your device to landscape orientation. So the amount of zeroes that a signature requires to start with consecutively determines how hard it is for miners how much hashing power or time it takes on average to find it. Jimi S. The mining node will need to test billions or trillions of nonce values before a nonce is found that satisfies the requirement. The central problem with a locktime is that the recipient of the transaction has no certainty that the transaction will be good when the locktime comes. The second is serialized imacros scripts bitcoin create bitcoin faucet rotator for site DER and is only 32 bytes. The sum of all inputs must be equal to or greater than pure js equihash miner how to deposit usd to bittrex and trade sum of all outputs. By agreeing you accept the use of cookies in accordance with our cookie policy. After the block reward is bitcoin symbol nyse zimbabwe news bitcoin inminers will rely solely on transaction fees to operate. If the average block time is below 10 minutes, the difficulty is increased. Linear, means that one direction is executed after the other consecutively.

Once the parent is received and linked into the existing chains, the orphan can be pulled out of the orphan pool and linked to the parent, making it part of a chain. Success with nonce Hash is f0ea21eb6dde5adb9da9f2bab2fcbca22b1e21a Elapsed Time: By evoking the extraction of precious metals, it focuses our attention on the reward for mining, the new bitcoins in each block. Whatever transactions remain in the memory pool are unconfirmed and are waiting to be recorded in a new block. A matching transaction in the pool, or in a block in the main branch, must exist. The final outcome is a bit alphanumeric hash. Another reason to avoid Turing completeness is that smart contracts with Turing completeness are very difficult to analyze. Technically, the time bitcoin fund fidelity coinbase support email address by a miner or a mining pool to discover a new block is directly proportional to the total processing power of the network, which in other words in known as hash rate. With a complete system, it is easy to create unintended behavior, causing bugs. New transactions are added to this 14 gpu mining rig frames dash instantsend coin through "blocks", which are created by miners using [mining]. InBitcoin BTC implemented a new feature called "Replace By Fee" RBF which basically allows you to rebroadcast a transaction that is stuck in the mempool with a higher transaction fee.
The mining node will need to test billions or trillions of nonce values before a nonce is found that satisfies the requirement. Transactions are designed so that ownership is passed from one address to the next. It started at 50 bitcoin per block in January of and halved to 25 bitcoin per block in November of The signature then becomes part of the newly updated transaction history. For high-value items, payment by bitcoin will still be convenient and efficient even if the buyer has to wait 24 hours for delivery, which would ensure confirmations. Supply of bitcoin currency over time based on a geometrically decreasing issuance rate. Converted to seconds, that is 3. We all know that Bitcoin is an open source, decentralized digital currency where the miners, who are part of the Bitcoin community contribute processing power to discover new blocks and confirm transactions over the network. That means that the corresponding private key must create a valid cryptographic signature when hashed. A transaction will likely include a collection of transactions. Bitcoin addresses are made up of the following three parts: The next few hexadecimal digits are used to encode an extra nonce see The Extra Nonce Solution , or random value, used to find a suitable proof of work solution. All Rights Reserved. The sender can perform a double spend attack and get their funds back. The public key is hashed from the private key, and then the private key confirms ownership of the corresponding public address.
Stay ahead with the world's most comprehensive technology and business learning platform.
We use cookies to give you the best online experience. The way this article works is from a basic description of Bitcoin script to a much more detailed description, ending with some basic opcodes examples. All payments, votes and tips are processed on chain. Wallet software is expected to retransmit such transactions or reconstruct them with higher fees if they are not successfully executed within a reasonable amount of time. All bits are zero: The miners have to construct a perfect block, based on the shared rules that all nodes follow, and mine it with a correct solution to the proof of work. Extract the coinbase data from the genesis block. The major difference between Bitcoin and traditional currencies is that not only is Bitcoin not a physical coin. For pool miners, this is an important consideration, because a full node requires a dedicated computer with at least 15 to 20 GB of persistent storage disk and at least 2 GB of memory RAM. However, there are several reasons that Bitcoin script does not loop, this is an important feature for program execution, and avoiding bugs. They also indicate the amount of coin that is sent, along with the address of the recipient. Assembling and Selecting Chains of Blocks. Eventually a transaction without fees might reach a high enough priority to be included in the block for free.
All transactions are deemed valid based on the most current state of the blockchain. When a block is created, the traffic light will turn green and the bus will turn towards the road with the blockchain writing on it. When it comes to the contents of a transaction, Bitcoin script is a fairly basic programming language and computational processes. In previous sections we saw how the miners get gridseed g blade litecoin miner buying cryptocurrency on black friday write a transaction geforce gtx970 msi zcash miner zencash masternode release awards them the new bitcoins created within the block and claim the transaction fees. Its application is central to the creation and security of the cryptographic signature. Each node that receives a valid block will incorporate it into its blockchain, extending the blockchain by one block. Here is an example:. They have specialized circuits that churn out a lot of processing power. Thus if a transaction has already been added to the block, it cannot be spent. Successful blocks pay the reward to a pool bitcoin address, rather than individual miners. Any donation is greatly appreciated! Bugs in a smart contract make coins vulnerable to unintentional spending. Reject if the sum of input values is less than sum of output values. Both of these blocks are children of the blue block, meant to extend the chain cryptocurrency how to invest trading cryptocurrency on leverage building on top of the blue block. Say that Alice wants to provide conditions under which Bob receives his Bitcoin. Guide to Cryptocurrency Arbitrage:
The header of the candidate block is then sent to each of the pool miners as a template. Bytes Per Second: A single Script program with an infinite loop could take down Bitcoin. Because the input is the output of the previous transaction, the public ledger and the transaction records indicate how all Bitcoin transactions came to be in the ownership of a specific address. Who is Vitalik Buterin? The topics begin with the most basic, and progress to the more complex:. In numerical terms, that means finding a hash value that is less than 0x Prioritized transactions can be sent bitcoin wallet info buy litecoin with echeck any fees, if there is enough space in the block. The increase comes from segwit transactions, which have their raw transaction data and signatures who has earned the most investing in cryptocurrency bitcoin vs ethereum transaction time. The ratio between the actual timespan and desired timespan is calculated and a corresponding adjustment up or down is made to the difficulty. In contrast, selling a more expensive item for bitcoin runs the risk of a double-spend attack, where the buyer broadcasts a competing transaction that spends the same inputs UTXO and cancels the payment to the merchant. The generation transaction is listed as the first transaction in the block. Bitcoin transactions do not have an expiration time-out. The maximum number of halvings allowed is 64, so the code imposes a zero reward return only the fees if the 64 halvings is exceeded. But Alice shares her public key is with Bob, and both addresses are publicly available. Pop removes the most recent element added to the stack. High-performance mining systems are albert murphy cryptocurrency trader cnbc crypto as efficient as possible with the current generation of silicon fabrication, converting electricity into hashing computation at the highest rate possible. Not a transaction hash reference. How, then, is such an adjustment made in a completely decentralized network?
This is how segwit achieves backwards compatibility with the 1mb block size limit. A cryptographically generated alphanumeric sequence is produced to prove the operation occurred. Here is an example:. Here is a slightly more detailed description of the processes of a Bitcoin Transaction. Reverse the order of the bytes and the result is 0xb44 , which is , in decimal. Once a node has validated a new block, it will then attempt to assemble a chain by connecting the block to the existing blockchain. Nevertheless, you should feel pretty comfortable with the fundamentals of Bitcoin Script by the time we are done. After a while, this would trigger the mining difficulty to go up as well, so that even with this extra hashing power, the block production rate will maintain a steady pace of 1 block per 10 minutes. Unless you throw double-six, you win. DUP opcode: For example, if a user sends 2 bitcoins in a transaction, but they have a UTXO of 10 bitcoin, the entire 10 bitcoins are sent. It took 13 attempts to find it. A rather simple answer indeed, but it makes sense.
Miners validate new transactions and record them on the global ledger. Last week, the difficulty levels went up by over 7 percent. What is Locktime? They can theoretically be as short as 26 characters if the public key that generates them starts with a series of leading zeros. I want something from John, so I pay John for his services rendered with a currency we have both agreed upon. As the newly solved block moves across the network, each node performs a series of tests to validate it before propagating it to its peers. Unlike Jing, some miners mine without a full node, as we will see in Mining Pools. In previous sections we saw how the miners get to write a transaction that awards them the new bitcoins created within the block and claim the transaction fees. A digital signature is a cryptographically generated code. The basic difference is obviously the size, and increased ease of managing the data. Was this article helpful? German automotive components company Bosch have disclosed they are running trials using the This is the process of converting the internal representation of the data structure into a format that can be transmitted one byte at a time.
